- Solutions
-
- File Server: Ransomware Protection
- File Server: File Copy
- File Server: Audit File Access
- File Server: Storage growth reporting
- Licensing/Pricing
- Contact
The Endpoint Operations page is designed to let you quickly apply configuration changes to many Endpoints at once. The key to this is Endpoint Information filter box at the top. Using this you can filter on many different fields (hostname, ip address, username, software version, etc) on the Endpoint. In the example below, "83.5" was entered, and any Endpoint that has that in the name, IP address or other information is shown. In this case, the filter found a few Endpoints that contain that in their IP address.

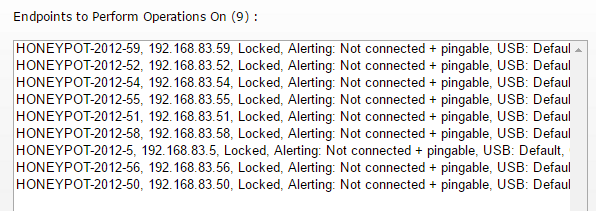
The number of selected Endpoints is shown in parenthesis (9 in the example above).
There are also some short-cut links that let you quickly filter on additional settings and configuration data.
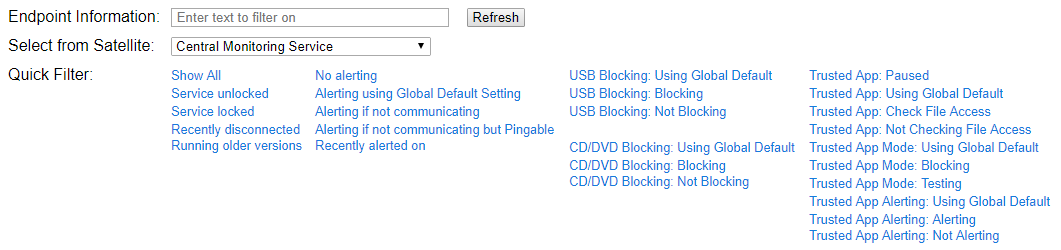
Once the target set of Endpoints has been selected, there are a number of different operations that can be performed by using the options on the right side of the selected Endpoint list.
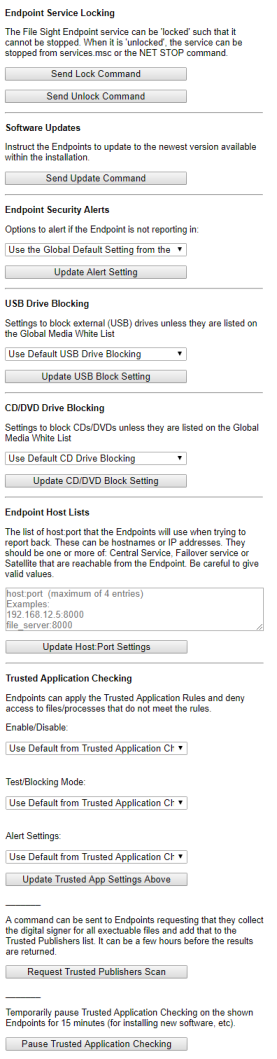
Endpoint Service LockingWhen an Endpoint Service is locked, it cannot be stopped from the Windows Service Control Manager (services.msc) or the net stop command. This prevents end-users from preventing file copy tracking. Software UpdatesThis is a simple way to tell Endpoints to update to the same software version as the Central Monitoring Service or Satellite that the Endpoint is connected to. Note that there is a shortcut filter "Running older versions" to easily select those Endpoints that need to be updated. Endpoint Security AlertsThe Endpoint Alerts page lets you set the Global Default alert setting. This option lets you set a specific alert setting to the filtered list of Endpoints. You can change them to use the Global Default, or to a specific alert setting. Please see the Endpoint Alert settings page for more information. USB Drive BlockingUSB Drive Blocking lets you optionally block external USB drives from computers where the Endpoint is installed and running. The options are to only allow white listed external drives (that are defined on the USB/CD Drive Blocking page) and block everything else, block everything, or to block nothing. CD/DVD Drive BlockingThis option is very similar to the USB Drive Blocking option, except it operates on CDs/DVDs that are inserted into the Endpoint computer. The white listed discs can be specified on the same USB/CD Drive Blocking page as above. Endpoint Host ListsThis option will allow you to change where the Endpoints (listed on the left) will report back to, including upto 3 backup services. You could change them to report to a satellite and then to the central service as a backup, or any combination you need. Once you enter the hostname or IP address with the port number select the Update button to push the changes to the Endpoints. Trusted Application CheckingA variety of Trusted Application settings can be set on the Endpoints. When the Update Trusted App Settings Above button is pressed, the three shown settings ( Enable/Disable, Test/Blocking Mode AND Alert Settings) will all be sent to the selected Endpoints. Request Trusted Publishers ScanClicking this button will request that the selected Endpoints scan all .exe and .dll files on the system and collect the digital signatures from each, and then merge them into the Trusted Publishers list. This can take a while to complete. Pause Trusted Application CheckingClicking this button will send a command to the selected Endpoints to pause all Trusted Application checks for 15 minutes. This is useful when temporary unsigned files need to run, as is often the case when software is installed. Each click of the button will restart the 15 minute pause time. |
|