- Compare Editions
- Product Information
- Resources
- Licensing / Pricing
- Support
- Contact

PA File Sight can see what files clients are interacting with on the server, and can alert when a client is reading an unusually large number of files.
If the File Sight Endpoint is installed on the client, external (USB) drives can be blocked, and file copying can be detected more accurately which helps in Data Loss Prevention (DLP) efforts.
These features are only available in the Ultra Edition. Compare Ultra vs Lite to see the differences.
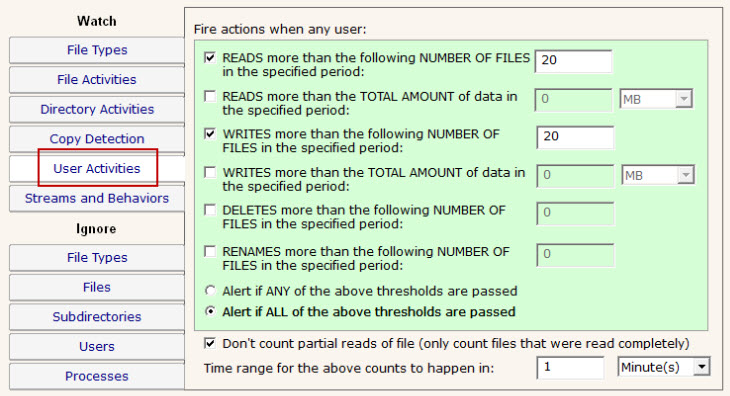
PA File Sight Ultra has a Watch User Activities tab. Here you can alert when a user Reads more than X amount of files in Y minutes. So considering that a typical office worker would only open perhaps 3-4 word documents in a 5 minute period, if you knew a worker had read 20 files from the server in those 5 minutes it is probably a situation where files are being copied.
This detection technique can provide alerts such as the following example:
Note that the above is careful to indicate it is alerting on files being read from the server. The server has no way of knowing where the files go on the client computer. They might get loaded into Word, or attached to an email, or copied to a USB thumb drive.
To better help determine where/how server files are being used on a client computer, the File Sight Endpoint can be installed on end user computers. This is a silent service that runs in the background. When files are retrieved from a file server, the File Sight Endpoint can provide additional information such as what process loaded the file (Word.exe, Explorer.exe, WinZip.exe, etc) and where that process is saving files.
In this example, the plain text is what the alert looks like without the Endpoint, and the bold text shows the additional information available when the Endpoint is running:
With this complete picture, it is now clear that in this example user Bob has copied a file from the file server to a local F: drive.
* Note that the client and server computers both need to be Windows 7 / 2008 R2 or newer for the Endpoint to detect file copying. Older versions of Windows did not communicate the client IP address.
In the example above, File Sight on the server sees that Expenses.xls was read, and asks the Endpoint for more information. The Endpoint sees a file named Expenses.xls was read from the server, and a file of the same name was saved to the F:\stealing folder using Windows Explorer (the same process that read the file from the server).
This appears to be a file copy operation, however the contents of the two files are not compared, so it's not 100% guaranteed to be a file copy, and that is why it is labeled a "Probable Copy".
If the the process was WinZip.exe and the output file was F:\stealing\Documents.zip, this operation would not be tagged as a Probable Copy, but the WinZip.exe process and outgoing filename of F:\stealing\Documents.zip would still be saved to the database for reports later.
Seeing true[2] is fairly rare. This scenario is similar to the true scenario above, except in this circumstance the Endpoint did not see the file being read from the server, but it did see the file being saved. An example of this happening would be if a user copied the file in an RDP session, and then pasted it locally. In that case the file was transfered "out-of-band", meaning not through the Windows SMB protocol.
The Trusted Application feature allows checking all file I/O against rules and blocking that which doesn't meet the rules. It is simple to add a rule that prevents writing to a local cloud drive (DropBox, Google Drive and OneDrive are currently supported), or preventing a write to a USB drive.
You could also create a rule indicating browsers (Chrome.exe for example) is not allowed to read .docx (Word document) files to help prevent them from being attached to an email or uploaded to a website.
Besides helping with copy detection, the File Sight Endpoint can also block USB/external drives on client computers, to prevent files being copied to those drives.
A global white list exists for drives/discs that are allowed for special cases. Read more about drive blocking.
PA File Sight can block a client account so it cannot access any more files on the server using the Add to Blocked User List action. This will prevent the user from accessing any more files on the server, while still allowing other users to continue their work with the server.
The Blocked Users List is actively shared among servers protected within the same PA File Sight installation, so other servers can be protected from this client account before he tried to copy files from them.
Read more about limitations and nuances to detecting file copying here.
“I love the new features... Thanks again for a great product!”
Adam Andonian, Nexius Inc, USA