- Solutions
-
- File Server: Ransomware Protection
- File Server: File Copy
- File Server: Audit File Access
- File Server: Storage growth reporting
- Licensing/Pricing
- Contact
Understanding how Alert Suppression, Event Escalation, and Event Deduplication work together can give you the tools to have fine grained control over your alerting environment.
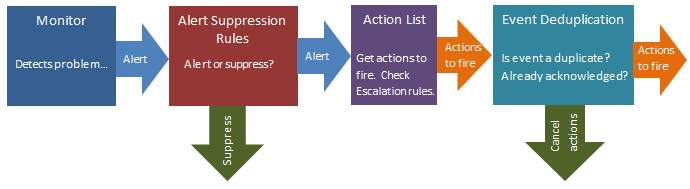
When a monitor first detects a problem, it consults with its Alert Suppression rules to determine whether the monitor should go into Alert state or not. So this is the first filter in the alert path. If the alert is suppressed, the monitor is not in Alert state and no further alerting is considered.
If a monitor is in Alert state at the end of it's check, it consults it's list of actions that might contain a list of Event Escalation alerts. This step is where the set of actions to run is determined. Event Escalation can be enabled and configured on a monitor-by-monitor basis.
There are two kinds of Event Deduplication -- Simple and Advanced. Below we'll discuss Advanced, as Simple doesn't have any affect on actions that are run.
After getting a list of possible actions to fire during the Event Escalation step, the alert is check to see if it is a 'new' alert. If it is new, the actions are fired as normal. But, if the event is not 'new', that means it's a duplicate. 'New' and 'duplicate' are determined by looking at fields in the event.
If an event is a duplicate: