- Solutions
-
- File Server: Ransomware Protection
- File Server: File Copy
- File Server: Audit File Access
- File Server: Storage growth reporting
- Licensing/Pricing
- Contact
File Integrity Monitoring, also called FIM for short, is a process for ensuring your important files have not been tampered with. This can be for things like documents and web site files, but also for application files and audit log files.
There are usually two types of integrity you want to watch for - unauthorized changes, and limited changes.
Some examples of unauthorized file changes would include:
The last two options, watching web sites, applications, and the operating system files, is also known as Intrusion Detection. Systems that can watch for these changes are sometimes called Intruction Detection Systems (IDS) or Host-based Intruction Detectoin Systems (HIDS).
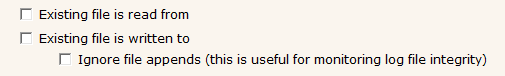
The other type of File Integrity Monitoring is to watch files that should change, but ensure they are changing in the correct way. The typical example of this would be log files that record ongoing actions in a system. The log file is regularly appended to, adding activity logs of recent activity. If someone wanted to cover their tracks, they would want to remove some lines in the logs that showed what they had done - so a change to the middle of the file (unauthorized) vs an authorized append-only change to the file.
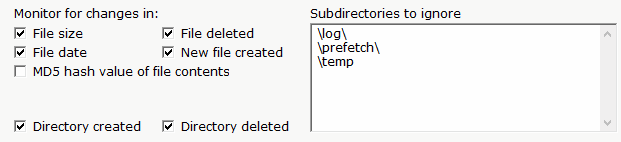
There are many solutions to both types of File Integrity Monitoring. The File & Directory Change Monitor is one exmaple that can watch for and report on changes to files (watching for the Unauthorized Changes category).
To watch for some changes (changes to the middle of a log file) but ignore limited changes (appends to the end) requires a more sophisticated system such as PA File Sight which has this ability built in.
Though not technically File Integrity Monitoring, another related concept is keeping track of data and making sure it doesn't leave the company. This might be called Information Monitoring and generally refers to ensure company files are not copied and taken such as on a USB drive. PA File Sight has capabililties in this area as well.
“That worked. You guys have the best customer service.”
Mary B., CIMTechniques, Inc., USA