- Solutions
-
- File Server: Ransomware Protection
- File Server: File Copy
- File Server: Audit File Access
- File Server: Storage growth reporting
- Licensing/Pricing
- Contact
NOTE: Event Escalation is only available in the Pro and Ultra editions.
State monitors (like the one shown below) support event escalation. This means that after a specified amount of time, additional actions will be run if the monitor is still in an error state.
When you attach the first action to an escalation item, a new escalation item will be added below the current escalation item, which you are free to use or ignore (that is, leave empty). The delay time that is preset for this action is automatically guessed -- you are free to change it.
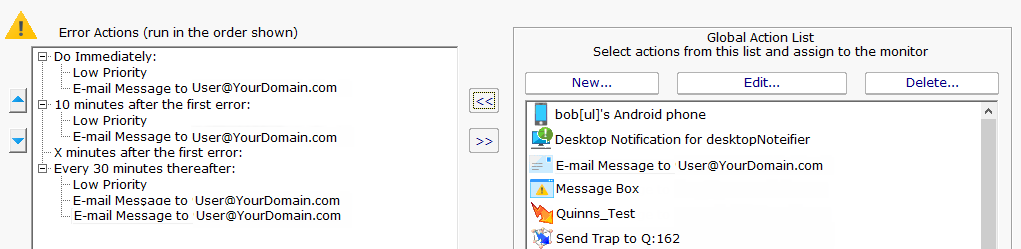
You may configure a particular escalation group by first clicking on the Escalation node to select it. This configuration may consist of changing the time at which the escalation group's actions are activated. You can configure an escalation period by hand editing the time shown in it. To do so, press the F2 key or click on the node a second time after selecting it, to "open" the node for renaming (exactly as you would with a file or folder name in Windows Explorer.) You can then enter a time value, which consists of a whole decimal number (no decimal point) followed by one of these time units: minutes, hours, or days. You do not need to type the "after the first error" portion.
Examples of correct escalation time setting text:
PA Server Monitor will always revise the text to read "XX minutes after the first error:" once you close the editing of the node. A non-minutes value will be normalized to the correct number of minutes (for instance, "1 hour" becomes "60 minutes after the first error.") The escalation groups will be visually re-sorted in the order of the times that they contain when you complete your editing.
Any escalation groups that are created, but left empty, will automatically be removed when you leave the Actions dialog.
See Adding Actions for additional information.
See Alert Suppressing, Event Escalation and Event Deduplication to see how these features can be used together for suppressing alerts.