- Solutions
-
- File Server: Ransomware Protection
- File Server: File Copy
- File Server: Audit File Access
- File Server: Storage growth reporting
- Licensing/Pricing
- Contact
The Trusted Applications Monitor enabled the applicationn whitelisting/trusted application feature for the given server. Read more about:
When the monitor is enabled, the Trusted Application functionality will be active on the server. Disable or delete the monitor to stop the Trusted Application functionality. There is an approximate 30 second delay from disabling/deleting the monitor until the Trusted Application functionality is completely disabled.
The monitor allows specifying Test Mode (where file activity is not actually blocked) or Block Mode which is the production setting.
Alerting for blocked files can also be enabled.
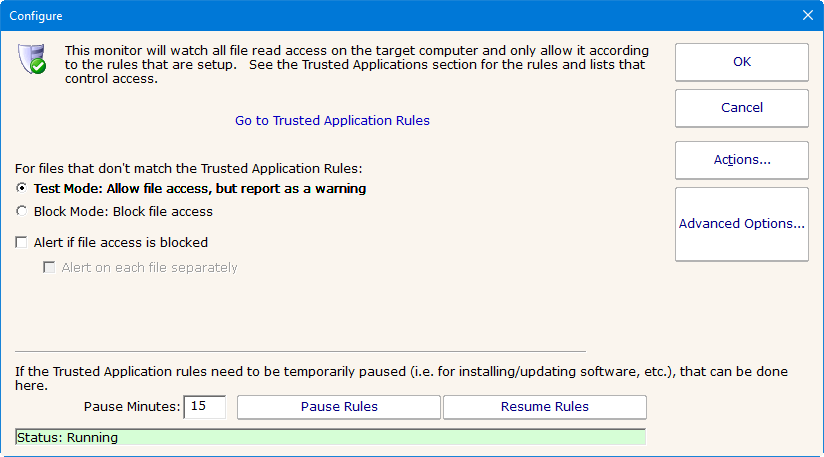
If you need to temporarily disable the monitoring and checking of a Trusted Application monitor, click the Pause Rules button. This is useful in situations where new software needs to be installed (sometimes installer components are not signed).
If you need to temporarily disable Trusted Applications on an Endpoint, go to Endpoint Services > Endpoint Operations. There you can filter the Endpoint list to just those you want to disable the checking on, and then click the "Pause Trusted Application Checking" button on the right. This will disable checking for 15 minutes.
Like all monitors, this monitor has standard buttons on the right for Adding Actions and setting Advanced Options.
When this monitor runs, it will record any files that are blocked for which reports can be run. There is also an interactive Trusted Applications Warning viewer that can be used to help fine tune the system.