- Solutions
-
- File Server: Ransomware Protection
- File Server: File Copy
- File Server: Audit File Access
- File Server: Storage growth reporting
- Licensing/Pricing
- Contact
Once you have the Trusted Applications feature up and running, and blocking access when it is not allowed, the day to day operations become fairly simple.
It is important to receive alerts when file access is blocked. Ideally, only malware would be blocked so file access alerts should be rare. If you get alerts that aren't malware, it might be a user trying to run a legitimate application that hasn't been allowed yet.
Typically you'll see an alert about a blocked (or test-blocked) application in the Access Warnings dialog. Since typical rules will allow access to files from the Trusted Applications list, the easiest thing to do is add the blocked application to the list. This can be done by clicking the green button as shown in the image below:
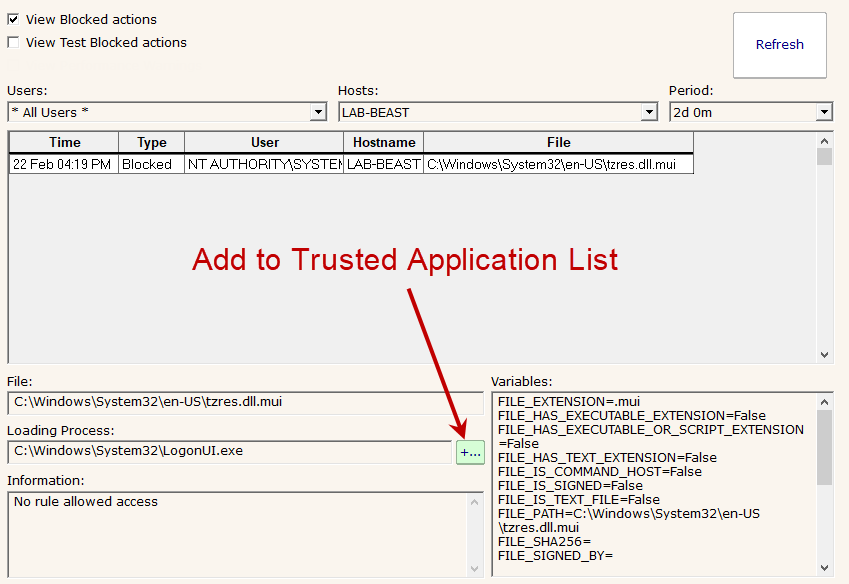
Clicking this button will send a query to the Central Service, Satellites, and Endpoints to get a list of signers, file sizes and file dates for that particular file. If the next attempt to launch matches those criteria, the application will be trusted and allowed to run.
To make warnings easier to look at, other warnings coming from the same application will be cleared since they probably wouldn't have happened now that the application is in the Trusted Application List.
Besides clicking the green button on the Access Warnings dialog as shown above, there are three other ways to allow legitimate applications to run:
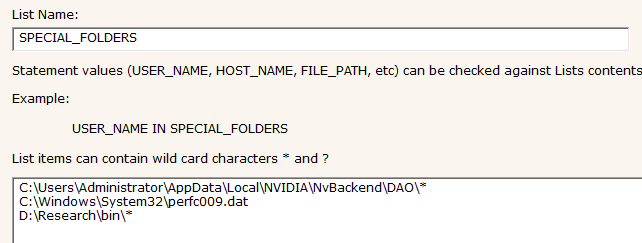 and this associated rule would allow applications in the above folders to run:
and this associated rule would allow applications in the above folders to run: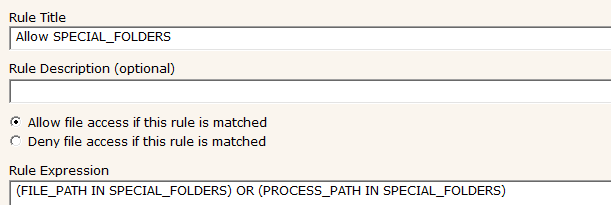 Note that the title of the rule can be anything - just the rule itself needs to refer to the Custom List name.
Note that the title of the rule can be anything - just the rule itself needs to refer to the Custom List name.
There might be times when the Trusted Application Rules need to be temporarily turned off such as when new software is installed or upgraded. To do this: