- Compare Editions
- Product Information
- Resources
- Licensing / Pricing
- Support
- Contact
Back to Setup Guide for Ransomware Protection
This method will work with all version of PA File Sight, not just the Ultra version.
The idea behind a honeypot is to create something tempting that only a ransomware application would touch, and something that humans should know not to touch. Typically this will be hidden folders with various files that would be tempting targets.
Often these folders are named something like aaaHoneyPot in hopes that the ransomware will scan that folder first (since it would sort to the top of a folder list). Unfortunately, there is no guarantee what order a ransomware will attack folders. In addition, at some point ransomware authors will get wiser and stop encrypting files in hidden folders. Even so, this is such a simple and inexpensive detection method it’s worth setting up.
Create a few hidden folders inside your target folder. In this example we’re protecting the D:\ folder, so create (for example) the following folders:
Make the folders hidden. Instruct your employees to never go into those folders.
Copy a few document files, spreadsheets, and PDFs into that folder. These should be files that are not critical, and could even be files you create now with non-important random data inside. Copy these files into both of the honeypot files mentioned above.
Now create two new File Sight monitors (one for each of the honey pot folders above). If they do, they might get blocked from the server.
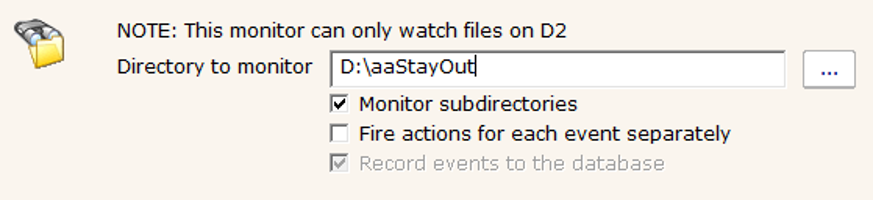
Watch all files on the File Types tab as shown below:
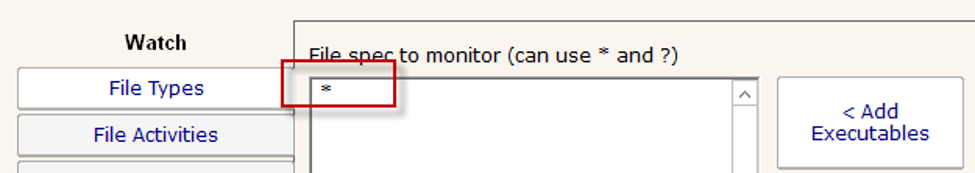
For the File Activities tab, we want to be notified (and run actions) if anyone reads any files in the honey pot folder:
All the rest of the Watch tabs can be left in their default state.
For the Ignore tabs, it's best to ignore anything that might generate 'noise'. For example, a backup application will likely read all the files. There is no reason to record all of that information to the database, so it's best to ignore the backup process. Ignoring the anti-virus application is probably a good idea too. If you don't see those processes listed yet, give it some time and come back to the monitor. PA File Sight will add processes to the list as it sees them.
IMPORTANT: Do NOT ignore the System or Network process. When a user accesses files from across the network, the 'process' they are using will be reported as "System or Network".
“I'm working in this industry for 15 years now, but I can hardly remember working with a software company with a support like you have. You listen and new features come really fast. I'm deeply impressed by your support and now have the feeling we made the 100% right choice to choose PA Server Monitor.”
Hanjo P., Pohlmann & Dimai GbR, Germany