By Des Nnochiri
PowerShell has long been a go-to utility for Windows network users, and Windows 7 remains a powerful player in the Microsoft ecosystem. Though the company plans to withdraw support for the operating system in 2020, Windows 7 is still the Windows variant of choice for many users across the globe.
It’s particularly popular in developing economies, where access to powerful hardware or the online connectivity needed to cope with the demands of Microsoft’s grueling schedules of Windows 10 updates simply aren’t available. Elsewhere, the ease of use, stronger privacy controls, and familiar interface of Windows 7 make it the preferred choice over Windows 10.
Whatever the circumstances, there’s still life in the old Windows 7 as of yet.
As for PowerShell, Microsoft’s task automation and configuration management framework has been open-source and cross-platform since August 2016 following the introduction of PowerShell Core. The utility retains its interface of a command-line shell and associated scripting language, from which administrative tasks are generally performed by “command-lets” or cmdlets.
(Image source: Wikipedia![]() )
)
The Need to Upgrade PowerShell on Windows 7
PowerShell cmdlets work by accessing data from different data stores, such as the Windows 7 file system or registry. These repositories are made available to the program through various providers, which now include third parties due to the open source nature of the utility.
Since its launch in 2006, PowerShell’s event logging functions have evolved considerably—to the extent that the Windows 10 version of PowerShell has much more robust logging than its earlier iterations. Upgrading a Windows 7 PowerShell installation to version 5.x of the program makes these capabilities available to users of the older operating system.
Installing PowerShell 5
Before installing PowerShell 5 on Windows 7![]() , it’s necessary to be running a system that already has Windows Management Framework 4.0 and the .NET Framework 4.5 installed. If you don’t have a pre-existing installation of either or both of these environments, you’ll need to install them first.
, it’s necessary to be running a system that already has Windows Management Framework 4.0 and the .NET Framework 4.5 installed. If you don’t have a pre-existing installation of either or both of these environments, you’ll need to install them first.
From that starting point, you can then install Windows Management Framework 5.1![]() , which includes essential updates to Windows PowerShell that allow (among other things) improved PowerShell usage auditing with Transcription and Logging and enhanced PowerShell Script Debugging.
, which includes essential updates to Windows PowerShell that allow (among other things) improved PowerShell usage auditing with Transcription and Logging and enhanced PowerShell Script Debugging.
Enabling Enhanced Logging
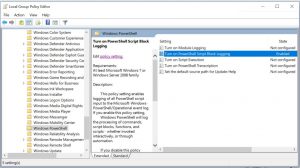
For Windows 7, enhanced logging may be enabled through Group Policy by going to Administrative Templates > Windows Components > Windows PowerShell. Settings may be configured as in the screenshot below.
(Image source: CSO Online)![]()
Configuration Options
The “Turn on Module logging” setting records portions of scripts and decrypted or de-obfuscated code. It logs events to event ID 4103 in the Windows PowerShell log. The Get-Module -ListAvailable PowerShell cmdlet displays a list of available modules from which you can choose the specific ones that you wish to track. If you wish to audit all the available modules in a system, use the wildcard variable (*).
“Turn on PowerShell Script Block logging” records whenever blocks of code are executed and is instrumental in guarding against cyber-attacks or insertions of malicious code in your network environment. Tracking is enabled for both complete scripts and individual commands.
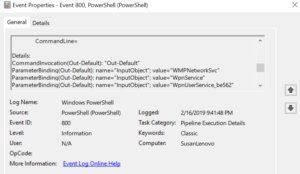
PowerShell Transcription logging is another option that’s useful in identifying potential avenues of attack. It provides a real-time transcript of each PowerShell session with input and output events.
(Image source: CSO Online![]() )
)
For best results, the PowerShell event log should be as large as possible, one gigabyte of storage being the optimum desirable for a Windows 7 network environment. Ideally, log files should be exported from machines for later review in sensitive or secure environments.
(Image source: CSO Online![]() )
)
PowerShell Security Scripts
PowerShell provides full access to COM and WMI, enabling administrators to perform administrative tasks on Windows systems both locally and remotely. In addition, WS-Management and CIM enabling management of remote Linux systems and network devices may be coordinated through PowerShell. The PowerShell hosting API (application programming interface) allows the PowerShell runtime to be embedded inside other applications.
Features like this can increase the exposure of a network to attack vectors, so take precautionary steps to prevent or mitigate such attacks. PowerShell’s scripting and automation capabilities can assist in this. Following Microsoft’s purchase of Github in June 2018, PowerShell users now have access to an extensive library of third party security scripts![]() , including the examples described below.
, including the examples described below.
POSH-Sysmon
Microsoft’s Sysmon (system monitor) tool monitors systems and adds fine controls for configuring events to be tracked, even after a reboot. The PowerShell POSH-Sysmon script is based on PowerShell 3.0 or above and enables the use of PowerShell to create and manage Sysinternals Sysmon v2.0 configuration files. Events collected by the system monitor may be later analyzed and checked for malicious or anomalous activity.
Remove-LocalAdmins Masive
The Remove-LocalAdmins Masive script enables network administrators to remove common local administrator passwords, which are often stolen and exploited by cyber criminals to facilitate sideways attacks across a network. The script analyzes all the computers specified in a given text file, looking for all the users listed in another file and then removes those users.
SecurityPolicyDsc
The PowerShell SecurityPolicyDsc script can be used to set local security policies based on internal company practices and external recommendations, such as those from the Center for Internet Security. Once a standard workstation has been set up according to these policies and tested, PowerShell may also be used to recreate those settings across your organization.
Posh-SecMod for Network Discovery
Posh-SecMod consists of a bundle of scripts dedicated to the task of network discovery: reviewing what outsiders can see on your network and revealing how this knowledge might be exploited. Its modules include tools for general network discovery, scanning system registries, database functions, and system auditing.
MicroBurst for Cloud Protection
MicroBurst consists of a collection of PowerShell scripts that can be used for the security penetration testing of Azure cloud deployments. The scripts support Azure Services discovery, weak configuration auditing, and post-exploitation actions, such as credential dumping.
With an installation of PowerShell 5.x in place—and the judicious use of customized scripts—it’s possible to enjoy enhanced system logging and to securely automate your Windows 7 network environment.