-

Dealing with DDoS Attacks Q & A
“You can’t fully protect yourself from DDoS attacks” – 1 on 1 with website security specialist, Igal Zeifman, from Incapsula. DDoS attacks are constantly starring in the tech news world. For those of you who have been living on a different planet – Distributed Denial of Service Attack, or DDoS attacks are malicious attempts to…
-

Does Windows Defender offer enough protection?
All Windows 8 computers now ship with Windows Defender installed. Based on Microsoft Security Essentials, it offers your devices basic protection across the board from malware, spyware and viruses. But it’s important to consider whether Defender alone will be enough to protect your computers from attack. It’s easy to be complacent about web security, but…
-
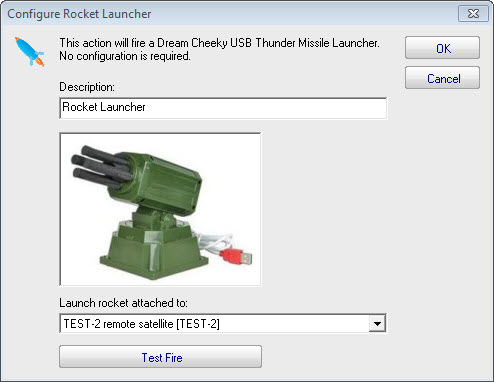
USB Rocket Launcher as an Alert
Think server monitoring can’t be fun? Think again! Try out our USB Rocket Launcher alert. PA Server Monitor can launch small USB rockets as an alert type. 🙂 The Dream Cheeky Thunder USB Missile Launcher (purchased separately) can be attached to the server where the PA Server Monitor is installed via the USB cable. The…
-

Everything You Need to Know About PCI DSS Compliance
Data protection for businesses in the modern, connected world is now more important than ever. It’s not always easy to protect data and all too easy to fall into the traps set by hackers and malware authors, especially when it comes to staff, who often inadvertently click on phishing links. For those companies that accept…
-
Are Windows 9 Rumors True?
Microsoft is set to announce Windows 9 at the Build 2014 Conference Windows 8 wasn’t exactly a resounding success. Much of what was updated in the OS was necessary, but the application of the new features was in many instances poor. Windows 8 attempted to stitch together the desktop and mobile experiences and this was…
-

How Can Server Monitoring Improve Performance?
It’s important to maintain a careful watch over a company server as misuse of this technology can lead to data loss and it can incur financial costs. Server monitoring tools provide administrators with an easy way to maintain a vigilant approach as they provide alerts and function to keep the administrator up to date and…
-

Windows 8 Review-Top 5 Reasons it’s Better
We’ve had several articles here on Network Wrangler pointing out the shortcomings and annoyances of the latest Windows OS. So, to be fair, we had Andrew Buckmaster give us his perspective on some of the things that he loves about Windows 8. And he makes some very valid arguments. Read on below for his review,…
-

Server Monitoring Best Practices
As a business, you may be running many on-site or Web-based applications and services. Security, data handling, transaction support, load balancing, or the management of large distributed systems. The deployment of these will depend on the condition of your servers. So it’s vital for you to continuously monitor their health and performance. Here are some…
-

Ensuring HIPAA Compliance
HIPAA sets the standards for the protection of PHI (Private Health Information) and ePHI belonging to those people who receive medical care from your business. So, if you are: A covered healthcare provider like a hospital or individual medial practitioner A business associate of these providers (including the private sector or 3rd party administrator) A…
-
Configuring VPN connections on a Windows Server
With the expansion of the Internet and the development of new technologies, VPN or Virtual Private Connections has become an important factor in all enterprises. This technology allows companies to interconnect different networks that are geographically separated to provide one massive intranet. Another important aspect is that VPN connections allow remote users to access internal…
Got any book recommendations?