-

The 9 Greatest Pain Points for an IT team
Those brave soldiers tasked with managing the IT systems of an organization are faced with myriad issues on a day to day basis. IT infrastructure cares not one iota for budget restrictions or staff reductions and will continue to behave like needy children in constant need of attention. This is to say nothing of […]
-

How Has Mobile Technology Impacted Data Security?
Mobile technology has fundamentally changed the way day to day business is carried out – of this there is little doubt. No longer is business restricted to the place of work or normal working hours. Conference calls can be made from almost anywhere, emails can be sent and received, and files can be shared with […]
-

Best Practices for Monitoring Oracle Database
As administrators, the responsibility for keeping a database running smoothly extends to satisfying not only the demands of users but also the requirements of senior management and the enterprise as a whole. In an Oracle environment, this requires setting up an infrastructure for monitoring the system that hinges on the objectives laid down by […]
-
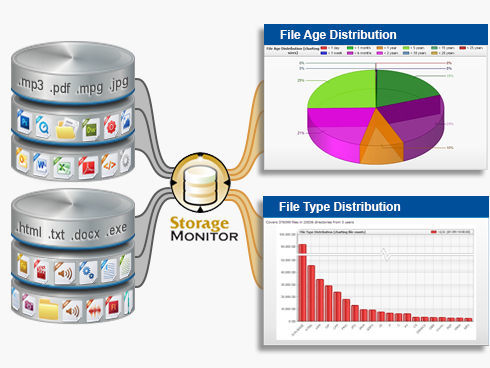
PA Storage Monitor version 6 Beta!
PA Storage Monitor version 6 has entered Beta! Exciting new features in version 6 include: Monitor template support PagerDuty alert action Desktop notification widget Configurable charts with configurable scaling Icons for servers and groups Dynamic server lists and groups based on server properties and more… You can find more information here. The PA […]
-

Best Practices for Monitoring Microsoft Sharepoint
With “collaboration” a watchword for much of business practice today, and online platforms providing the environment in which it takes place, it’s essential to ensure that your working data is available and secure. For Windows users especially, Microsoft SharePoint is the platform of choice. This guide will help in monitoring and maintaining your SharePoint […]
-
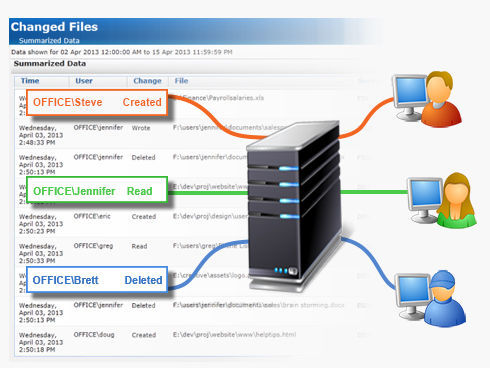
PA File Sight version 6 Beta!
PA File Sight version 6 is now in Beta! For those not yet in the know, PA File Sight tracks who is accessing files on a Windows server. Lots of software can tell you who created or saved a file. Almost no products can tell you who is reading from a while, or who deleted […]
-
Simulating a Large Network
We live, eat, breathe and love monitoring here at Power Admin. So we’re always looking for ways to improve. One way is to scale our software to handle ever increasing loads. Some of our larger customers (the largest anti-virus and computer security software company in America which starts with ‘Sym’ and ends with […]
-
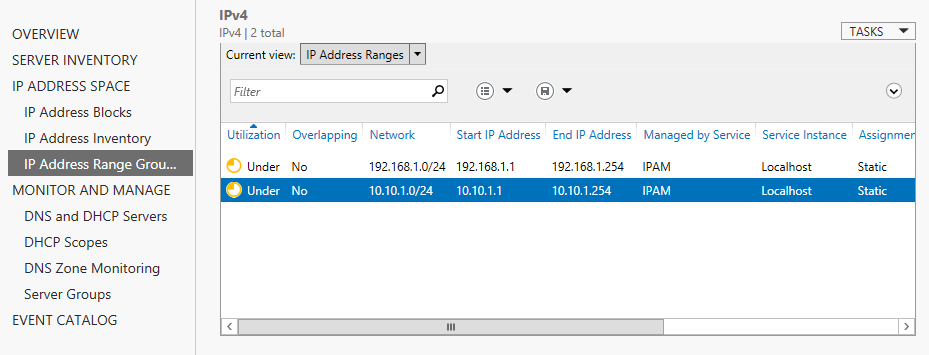
Configuring IPAM IP address spaces
In our previous IPAM article we’ve started discussing about this brand new technology that was introduced with the release of Windows Server 2012. We’ve seen how to install and configure IPAM and we’ve also managed to add a server to our IPAM database. In this article I want to further dive into the features that […]
-

7 Simple Steps to Configure IPAM in Windows Server 2012
IP address management (IPAM) is a new feature introduced in Windows Server 2012 that allows you to configure, manage and have a general overview of the network’s IP addresses and ranges. With IPAM, you can search for desired IP addresses and ranges, manage and configure DHCP scopes and DNS entries, view the status of your […]
-
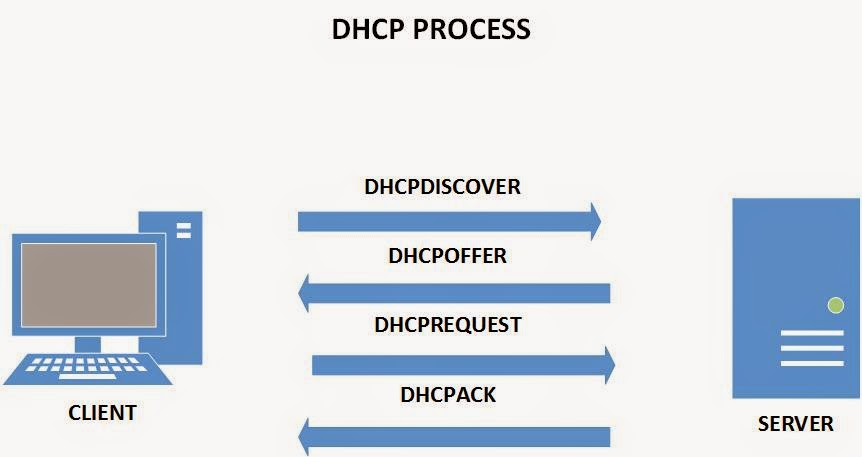
How to install and configure a DHCP Server on a Linux machine – Part 2
Hi folks, In the previous article we’ve configured a CentOS machine and installed the DHCP package. We’ve then created a sample configuration file for our machine, but we haven’t finished deploying our DHCP server yet. In this article we’ll finish our configuration and hopefully, we’ll be able to obtain an IP address lease from our DHCP machine. […]
Got any book recommendations?