-
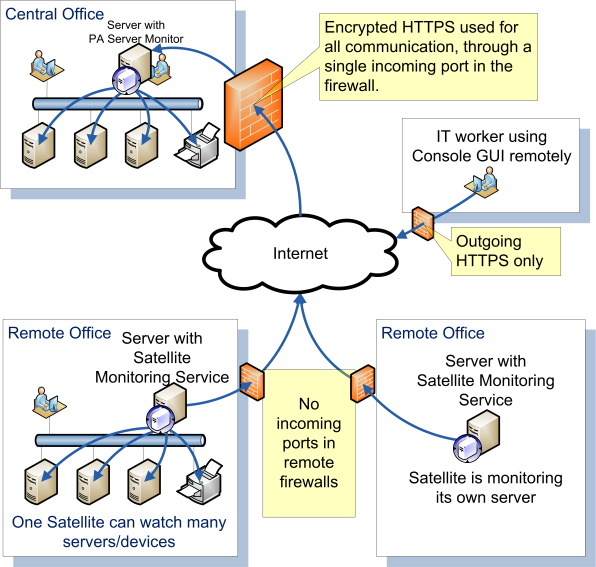
Free and Secure Remote Access? Sort of …
Recently, GoToMyPC forced all customers to reset their passwords. They were not hacked, but rather saw that hackers were attempting to access their customers’ computers using credentials that had been hacked from other places. This seems like a good opportunity to show off how PA Server Monitor can allow remote access in a completely […]
-

Machine Learning and Infrastructure Analytics, Part 2: Current Tools and Future Trends
In the first part of this report, we considered how the move to cloud-based resources for data storage, application delivery and infrastructure management is coinciding with the proliferation of new, smarter gadgets and monitoring devices – and the need to make sense of all the data that they produce. Learning systems based on […]
-

Machine Learning and Infrastructure Analytics, Part 1: Principles and Practices
Occasionally, parallel strands of technological development come together to yield unanticipated benefits in areas for which the technology was not specifically designed. Think of advances in the textile industry, during the Industrial Revolution. Or the genius of microwave popcorn. In this first of a two-part report, we’ll be looking at how the development of […]
-

Reducing the Risks of File Sharing
Exchanging ideas and sharing information are integral parts of working life. Ever since computers and digital technology became central to the way we work, people have exploited various means of passing documents and files containing text, images, and audio-visual data on to colleagues, suppliers and partners. As technologies have evolved, the methods have improved. […]
-

Another email Hack: Should We Worry?
Each time a major email service or social media platform gets hacked, the incident generates exciting headlines in the media. But behind the hype there’s a very real tale of anxiety for all the users concerned. Has vital information been stolen or compromised? Are funds being siphoned off, into the hands of criminals – […]
-

Best Practices for Software-Defined Storage
Currently being celebrated as the revolutionary new face of IT infrastructure, software-defined networks or SDNs have gained a lot of hype, but not too much practical guidance in the industry press. In this article, we’ll suggest some best practices to enable you to make the most of the data storage capabilities of this evolving technology. […]
-

What is Cryptolocker Ransomware?
Cryptolocker is a well known malware (software that does harm) of a particular variety: ransomware. Some malware (like computer viruses) delete and destroy. The hackers that create ransomware have other motivations: money. Ransomware Ransomware does something to your computer, and then demands a ransom payment to get your computer back to the way it used […]
-
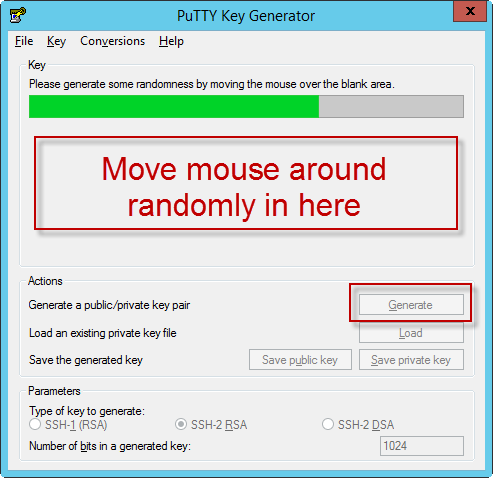
Enabling Public/Private Key SSH Authentication on VMWare ESXi from Windows
Having just struggled with this for a while, I thought I’d record the steps I took. They’re pretty easy once you figure them out (isn’t it always that way!). First, we need to enable SSH connections to our ESXi server. In the vSphere client, go to Security Profile. If you don’t see SSH, you can […]
-

Using Threat Intelligence Services to Enhance Security
Trying to recover from a cyber-assault or serious data breach can be a stressful and expensive affair. A far better approach is to make sure that your business is safe from such catastrophes before they occur – or at the very least, capable of staging a swift recovery in the event that disaster does strike. […]
-

Bring Your Own Everything Revisited
As advances in technology bring about a convergence of portable hardware, virtualized resources, and remotely hosted tools and platforms, there’s been a corresponding increase in the use of personal devices and related matters in the workplace and in public institutions. This trend has implications for the management, deployment, and security of IT resources – some […]
Got any book recommendations?