-
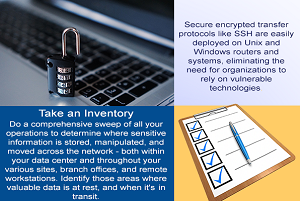
Enterprise Encryption Best Practices – Info Graphic
We hope you like this infographic. We’ll have a follow up article posted on October 18th with more information 🙂
-

Reducing Downtime While Backing Up AWS EC2 Instances
We’re big fans of AWS and use several of its services. One service we use is EC2 – it costs much less than having a dedicated server and still gives you full control of the server. One issue is being sure we can bring the server back up in case it crashes, or the…
-

15 Ways to Protect Your Business from Hackers
Today we have a guest post from Sachin over at FromDev.com. And without any further ado, we’ll turn it over to Sachin. There is no business in this internet age that cannot be hacked. Most skilled hackers can hack into any system. It has happened to most of the top tech businesses in the past,…
-

Next Generation Enterprise Campus Networks
Enterprise networks are no longer confined to simple client-server operations and application workloads, managed in-house. Internet connectivity, mobile workforces, Bring Your Own Device (BYOD) policies, social media integration, the Cloud and Big Data analytics are all contributing to an environment that demands greater versatility and efficiency from the enterprise campus. In this article, we’ll…
-
Endpoint Security Tips
With BYOD (Bring Your Own Device; either personal, or provided by the enterprise) now an integral part of policy in so many organisations, there’s an increased risk of USB flash drives, laptops, tablets, or smartphones holding sensitive data falling into the wrong hands – or being compromised in some way that allows malicious intruders to…
-

Why Network Monitoring is Important for Your Business …
Check out our post over at SiteProNews
-

Over the Edge?
As desktop and mobile owners continue to make a slow transition from previous versions of the operating system to Microsoft’s new Windows 10, enough user experience and feedback has emerged to give so me early assessments of the software giant’s flagship environment. In this article, we’ll be looking at one of the linchpins of…
-

Tips on Scaling Your Enterprise Storage
Over time, business conditions change, and the demand for capacity to accumulate and analyse information, applications and documents change. To keep up, your organisation needs the ability to adjust the magnitude of its storage and compute capacities. As hardware depreciates and traditional methods of storage get superseded by new techniques and technologies, you require…
-

The Costs of Not Monitoring
Why monitor your servers? As with all resources, computer resources are limited. That means limited work can done by the CPU, limited information can be held in system memory for use, and limited data can be stored on disk. When a system has all of the resources it needs, it generally runs fine. But…
-

Network Security: How to Avoid Physical Security Threats
In a 2015 study conducted by Ponemon Institute, a data security research organization, they found that the average total cost of a data breach incident was $3.8 million. In 2014, the average cost was only $3.5 million. In recent years, data breach has become increasingly common that many companies are stepping up their IT security…
Got any book recommendations?