-

Best Practices For Change Management
Making any kind of alteration to the way an organization runs its affairs is a process that’s fraught with the potential for risks and complications. Not only may the proposed modifications not have the desired effect, they may also meet with resistance or outright opposition from the very people required to put them in place,…
-
Comparisons of Azure vs Amazon AWS
Given the advantages offered in expanded infrastructure, increased computing power and data storage capacity, flexibility, time-saving, and decreased management and maintenance overheads, it’s easy to understand why growing numbers of enterprises are committing their resources to some form of cloud-based service or platform. Mention the words “cloud platform” in a commercial context, and two…
-
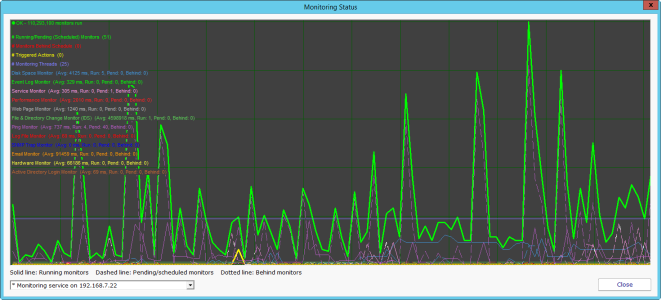
See Real-Time Monitoring Load
Did you know you can double-click the heartbeat chart in the upper-right corner of the Console to see an expanded version of that chart? The expanded version shows the various monitor types and which ones are currently running, which monitor types are behind, etc. As of version 7.4 it’s also possible to see this…
-
A Breakdown of the Various Kinds of Windows 10/2016, and the Upgrade ‘Rings’
With a significant number of users worldwide still clinging tenaciously to their installations of Windows 7 – and smaller number holding onto the markedly less popular Windows 8.x variants – Microsoft’s dream of a smooth and global transition to its latest desktop and network operating systems has yet to become a reality. But improvements…
-

GDPR and the UK Data Protection Bill
The GDPR and UK Data Protection Bill have some similar language to the PCI DSS involving keeping track of data and who/what process is accessing data. Specifically, Article 30 indicates data processors “shall maintain a record of all categories of processing activities“. Customers are beginning to turn to PA File Sight for help with this. …
-

A Windows Authentication Primer
Authentication. It sounds easy enough, in principle: You have a system, a procedure which anyone that tries to gain access to it has to follow, and a set of checks to ensure that recognized users are actually who they claim to be. But every system has its individual quirks – commercial operating systems, especially. …
-

How to Tell if Your Network Interface Controller is About to Go Bad, and What to do About It
With the whole world and everything in it being online these days, becoming disconnected from the internet is just about the worst thing that can happen to a person. Whether you are accessing the internet for business or pleasure, few things can make our blood boil like seeing the little yellow warning triangle pop up…
-

Backup Strategies For Data Centers
Even for the smallest scale enterprise, the practice of making regular, clean, and tested backups of essential information is fundamental to ensuring business continuity, data integrity, and security. When an organization is of a size that warrants the use of a full-blown data center, this ups the game considerably. After all, the information being…
-

Performance Characteristics To Watch On IIS
Internet Information Services (IIS, which was formerly known as Internet Information Server) is a flexible, general-purpose web server originally created by Microsoft for its Windows NT family of network operating systems. IIS supports a number of web protocols, including HTTP, HTTPS, FTP, FTPS, SMTP and NNTP. IIS is used on Windows systems to provide…
-

How to use Wireshark to diagnose network problems
Wireshark is distributed as a free open source packet analyzer. The utility provides a detailed report on the traffic flowing through your Network Interface Card (NIC), and may be used in benchmarking network performance and troubleshooting network issues. Here are some tips and best practices, describing how. First Steps If you haven’t done so already,…
Got any book recommendations?