Sometimes you need to check on the status of your applied updates and quickly. With news of the WannaCrypt/WannaCry Ransomware spreading via the MS17-010
Sometimes you need to check on the status of your applied updates and quickly. With news of the WannaCrypt/WannaCry Ransomware spreading via the MS17-010![]() vulnerability around the globe
vulnerability around the globe![]() it’s a good idea to double check that all your updates are applied correctly.
it’s a good idea to double check that all your updates are applied correctly.
The following is a quick PowerShell Execute Script monitor that you can add to Server Monitor to check for the presence of the HotFixes needed to mitigate MS17-010:
# KB4012598 KB4018466- Windows Server 2008
# KB4012217 KB4015551 KB4019216 - Windows Server 2012
# KB4012216 KB4015550 KB4019215 - Windows Server 2012 R2
# KB4013429 KB4019472 KB4015217 KB4015438 KB4016635 - Windows Server 2016
# List of all HotFixes containing the patch
$hotfixes = "KB4012598", "KB4018466", "KB4012217", "KB4015551", "KB4019216", "KB4012216", "KB4015550", "KB4019215", "KB4013429", "KB4019472", "KB4015217", "KB4015438", "KB4016635"
# Search for the HotFixes
$hotfix = Get-HotFix -ComputerName $mon.ComputerName | Where-Object {$hotfixes -contains $_.HotfixID} | Select-Object -property "HotFixID"
# See if the HotFix was found
if ($hotfix) {
$mon.FireActions = $false
$mon.Details = "Found HotFix: " + $hotfix.HotFixID
# a blank value removes the property
$mon.SetComputerCustomPropByID(0, "NEEDS-MS17-010-FIX", "")
} else {
$mon.FireActions = $true
$mon.Details = "Didn't Find HotFix"
$mon.SetComputerCustomPropByID(0, "NEEDS-MS17-010-FIX", "YES")
}
The script should work in either Powershell v2 or v4 and contains all the Hot Fix numbers as of 5/16/2017 that contain the MS17-010 patch (each rollup update will replace the existing HotFix with a new KB number).
If you are using another version of Windows not listed above or if you’re trying to apply this to another vulnerability, the process for getting the KB numbers for the $hotfixes variable is:
- 1 – Go to the Vulnerability’s page
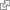 and locate the original KB number(s) for your systems
and locate the original KB number(s) for your systems - 2 – Use the original KB number(s) for the $hotfixes variable in the script above
- 3 – Go to the Windows Update Catalog
 and search for the KB number
and search for the KB number - 4- Click the matching update(s)
- 5 – Under the Package Details, add any KB numbers in the “This update has been replaced by the following updates” box to the $hotfixes variable
- 6 – Repeat steps 4 and 5 for each additional Hot Fix number until you get to the Hot Fix number(s) that haven’t been replaced yet.
- 7 – You should now have the full list of KB numbers that mitigate the vulnerability and you can deploy the script.
This is only a quick way to assess what systems are missing the fix right now. The current KB numbers will eventually be replaced as new Rollup updates get released and replace the previous ones. You can keep the HotFix List up to date by adding new KB Numbers to the $hotfixes variable, but hopefully once you know which systems are vulnerable you can make sure that they’re patched and remove the monitor entirely.
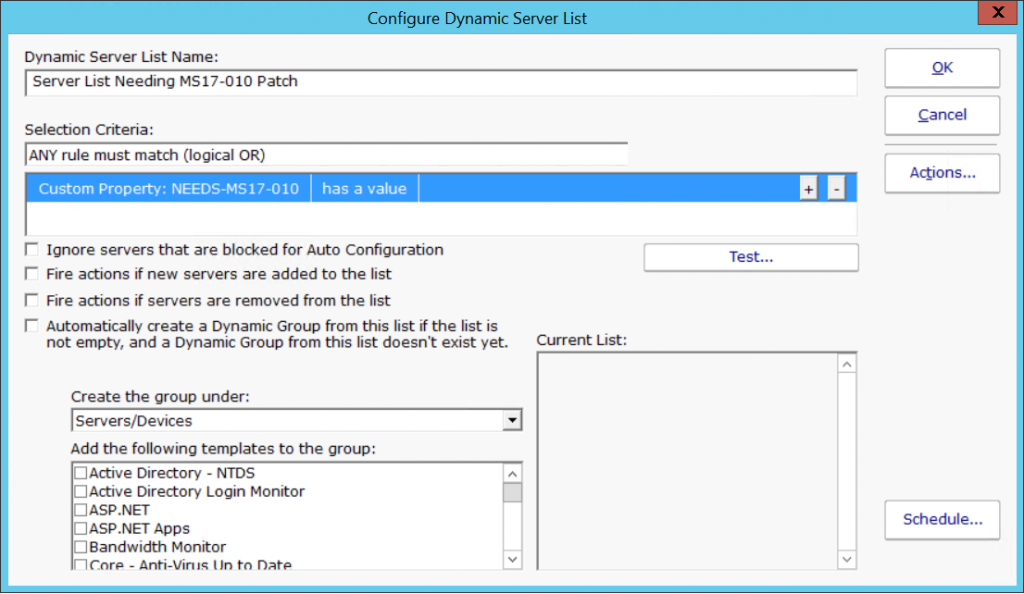
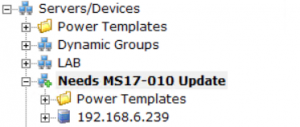
This script will fire alerts for each server that is missing the HotFix. It also sets a Custom Property on the server. With the Custom Property set, you could create a Dynamic Group that will automatically contain all of the servers that need the HotFix.
With the Dynamic Server List in place, you can create a Dynamic Group to easily see the servers that need to be updated.
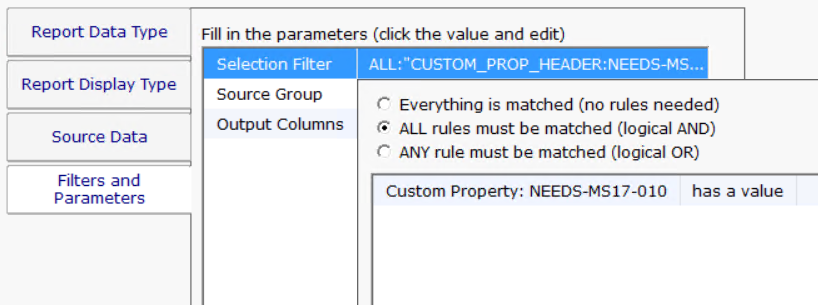
Finally, you can also run an Inventory Details report to get a list of affected server.