In the previous post, I mentioned a couple of ways customers are working on detecting CryptoLocker attacks. In this post, I’ll share a few scripts they use in response.
Ideally, you could quarantine the user’s computer from where the attack is coming from. In practice, that can be tricky.
Note that these responses could be used whether a computer is changing honeypot/canary files, or over activity thresholds that you have set.
Offense: Disconnect the User
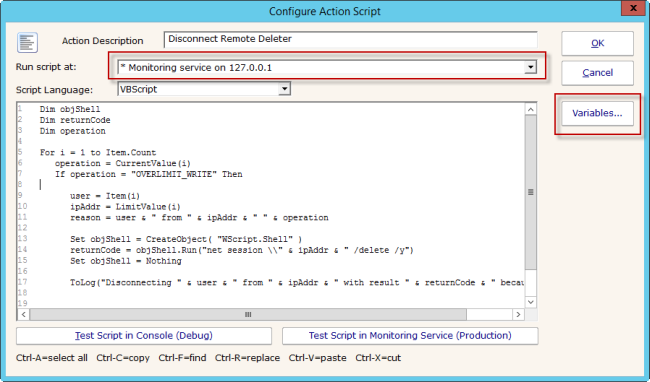
The following Execute Script action will disconnect a user from a share. It is watching for an alert about a user writing too many files (“OVERLIMIT_WRITE”). You could also look for other conditions like OVERLIMIT_READ, or even just READ.
Dim objShell
Dim returnCode
Dim operation
For i = 1 to Item.Count
operation = CurrentValue(i)
If operation = “OVERLIMIT_WRITE” Then
user = Item(i)
ipAddr = LimitValue(i)
reason = user & ” from ” & ipAddr & ” ” & operation
Set objShell = CreateObject( “WScript.Shell” )
returnCode = objShell.Run(“net session \\” & ipAddr & ” /delete /y”)
Set objShell = Nothing
ToLog(“Disconnecting ” & user & ” from ” & ipAddr & ” with result ” & returnCode & ” because ” & reason)
End if
Next
(note if copy/pasting – WordPress is changing the quote mark ” — it will need to be turned back into a normal simple quote mark)
Code
The For loop is necessary because a single alert can contain information about a variety of users and files, so you want to respond to just the appropriate users and files.
The Variables button on the action will show what variables are available and what they mean. That is where you’ll find other options for OVERLIMIT_WRITE, OVERLIMIT_READ, etc.
One important caveat: If you are using remote Satellite monitoring services, make sure the script is set to run at that Satellite, otherwise the Central Service will run it and possibly not be able to reach the intended client to disconnect them.
Caveats
Reconnects
Now for the bad news. In my testing, the NET SESSION /DELETE command does disconnect the user. But the client Windows OS has cached credentials, and it seems to reconnect immediately so further access can continue. Disconnecting at the router might be better but of course that would need to be a different command. If you have other disconnect ideas, please share them and I’ll add them here.
Older Windows Clients and Servers
Windows XP, 2003, Vista and 2008 versions of Windows do NOT send the IP Address of the requesting computer to the server. That means we have the user account to work with, but not an IP Address that can be targeted. If your server is 2003 or 2008, then it cannot receive the IP Address of the requesting computer. Sending that IP Address was part of the change to the SMB protocol that came with Windows 7 and Windows 2008 R2.
File Sight Version
We made an update to PA File Sight to give you the IP Address (if available) via the LimitValue variable in the row variables. You’ll need to use version 6.2.0.162 (the Preview build today) or newer.
Offense: Shutdown the User’s Computer
Another option is to shut down the attacking computer. Similar to the caveats above, the computer will need to be Windows, and Windows 7 or Server 2008 R2 or newer. Assuming this is the case, the following script will work:
Dim objShell
Dim returnCode
Dim user
Dim ipAddr
Dim reason
Dim operation
For i = 1 to Item.Count
operation = CurrentValue(i)
If operation = “OVERLIMIT_WRITE” Then
user = Item(i)
ipAddr = LimitValue(i)
reason = user & ” from ” & ipAddr & ” ” & operation
Set objShell = CreateObject( “WScript.Shell” )
returnCode = objShell.Run(“shutdown /s /m \\” & ipAddr & ” /c ” & Chr(34) & reason & Chr(34))
Set objShell = Nothing
ToLog(“Shut down ” & user & ” from ” & ipAddr & ” with result ” & returnCode & ” because ” & reason)
End if
Next
(note if copy/pasting – WordPress is changing the quote mark ” — it will need to be turned back into a normal simple quote mark)
Caveats
Windows only
This only works if the attacking operating system is Windows (the shutdown command is Windows specific), and PA File Sight has to have received the IP Address, which means it has to be Windows 7 or 2008 R2 or newer.
Older Windows Clients and Servers
Windows XP, 2003, Vista and 2008 versions of Windows do NOT send the IP Address of the requesting computer to the server. That means we have the user account to work with, but not an IP Address that can be targeted. If your server is 2003 or 2008, then it cannot receive the IP Address of the requesting computer. Sending that IP Address was part of the change to the SMB protocol that came with Windows 7 and Windows 2008 R2.
Account rights
The SHUTDOWN command will get run using the account that the PA File Sight service is running as. For it to successfully force a remote computer to shutdown, it needs administrator access to that computer. That implies that the PA File Sight service should run as a domain administrator account.
File Sight Version
We made an update to PA File Sight to give you the IP Address (if available) via the LimitValue variable in the row variables. You’ll need to use version 6.2.0.162 (the Preview build today) or newer.
Defense: Shutdown the Server
The Reboot Server action could be used to simply shutdown the server to protect it from attack. No caveats to this one, except that the server is down and users can’t access their files. But if the CryptoLocker virus has it’s way, they won’t be accessing them for long anyway.
Other Ideas?
If you have other ideas that have worked for you, please share them by sending us an email and we’ll add them here.