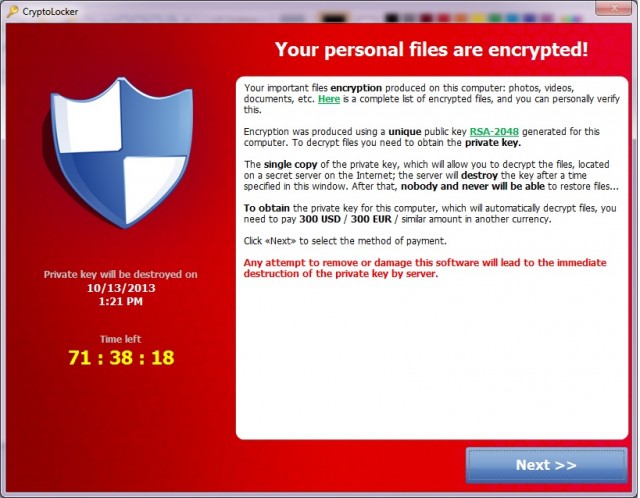
 In case you haven’t heard, CryptoLocker is a popular form of the ransomware malware that encrypts your files and then holds them hostage. Generally you have to pay to get them decrypted. If you have a backup of all of your data, you might be able to avoid the payment. If you have a backup…
In case you haven’t heard, CryptoLocker is a popular form of the ransomware malware that encrypts your files and then holds them hostage. Generally you have to pay to get them decrypted. If you have a backup of all of your data, you might be able to avoid the payment. If you have a backup…
What makes it worse is that CryptoLocker will lock any files that an infected computer can access, including files on the network. That means businesses with networks and shared folders (virtually all businesses) are at great risk. Do you have important shared folders with files that are accessed by many users? It just takes one user’s computer to get infected and all of those files could get encrytped 🙁
Clever Detection Solution
 We have brilliant customers. One of them, Eric, works at a large real estate management firm. His network has been hit a few times by CryptoLocker so he devised a clever means of detecting it quickly before it could do much damage. To do this, he uses PA File Sight.
We have brilliant customers. One of them, Eric, works at a large real estate management firm. His network has been hit a few times by CryptoLocker so he devised a clever means of detecting it quickly before it could do much damage. To do this, he uses PA File Sight.
CryptoLocker Honeypot aka CryptoLocker Canary
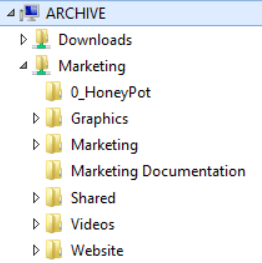 PA File Sight alerts you when files are accessed, which means written to, read from, created or deleted. Eric used this to his advantage by creating a ‘honeypot’ folder in his shared folders that people wouldn’t normally access, but which everyone had full access to. He loaded it up with typical files that might be in a folder like Word and Excel documents, PDFs, etc. Then, since some CryptoLocker applications will scan directories in alphabetical order, he named it so it would be at the front of the list. Employees were instructed not to touch any files in that folder.
PA File Sight alerts you when files are accessed, which means written to, read from, created or deleted. Eric used this to his advantage by creating a ‘honeypot’ folder in his shared folders that people wouldn’t normally access, but which everyone had full access to. He loaded it up with typical files that might be in a folder like Word and Excel documents, PDFs, etc. Then, since some CryptoLocker applications will scan directories in alphabetical order, he named it so it would be at the front of the list. Employees were instructed not to touch any files in that folder.
Next he installed PA File Sight and had it watch the honeypot folder. If any writes (such as writing a newly encrypted file to disk) happened in that folder, PA File Sight would send an alert. Eric also mentioned writing an Execute Script action that would disconnect the share to protect the files.
Ransomware Behavior Analysis
This was a great start, but Eric didn’t stop there. He used PA File Sight’s unique ability to alert when a user reads, writes or deletes more than a certain number of files within a set timeframe.
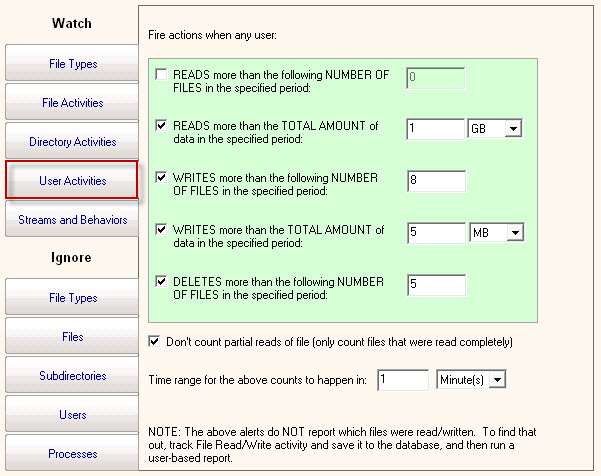 He set his threshold differently than the screenshot here — something like 50 file writes in 2 minutes. No normal user is going to be saving 50 files in 2 minutes! But CryptoLocker probably will — once it starts causing trouble, it needs to get as much done as quickly as it can. So when this file access behavior is detected, he had PA File Sight alert, and then run his script to disconnect the share. This allows him to watch the full share for those instances where CryptoLocker doesn’t read folders in alphabetical order.
He set his threshold differently than the screenshot here — something like 50 file writes in 2 minutes. No normal user is going to be saving 50 files in 2 minutes! But CryptoLocker probably will — once it starts causing trouble, it needs to get as much done as quickly as it can. So when this file access behavior is detected, he had PA File Sight alert, and then run his script to disconnect the share. This allows him to watch the full share for those instances where CryptoLocker doesn’t read folders in alphabetical order.
Eric reported that there were occasionally some false-positives when a user was doing something unexpected, but those few were well worth the time and money they saved preventing an all out CryptoLocker attack. In fact, just recently he was back purchasing more licenses so he could protect additional servers 🙂
Part two of this post will show some example scripts that could be used when a CryptoLocker attack is detected.
Another post lists file extensions that some people are using to detect current CryptLocker variants.