Category: Windows
-

5 Great Ransomware Removal Tools
Ransomware is one of the fastest growing security threats in the online world. Over the last few years, ransomware attacks have become increasingly common to the extent that these attacks have evolved into one of the most harmful forms of cyber attack there is. Ransomware attacks can target any PC user, whether it’s a […]
-

The best new features of Windows 10
To celebrate Windows 10’s first birthday, Microsoft has released an anniversary update to the software. If you’re already running with Windows 10, the update is free and features a number of upgrades to Microsoft’s PC software, including selfie login for websites and apps, and an unlocked Cortana. It also fixes a number of bugs and […]
-

Monitor (Failed) User Logins in Active Directory
Everyone knows you need to protect against hackers. How do you protect your computers from hackers? One way is to monitor for lots of failed login attempts. But how do you do that? With Windows, you watch the Security Event Log – there are many, many events related to users logging in, failing to […]
-
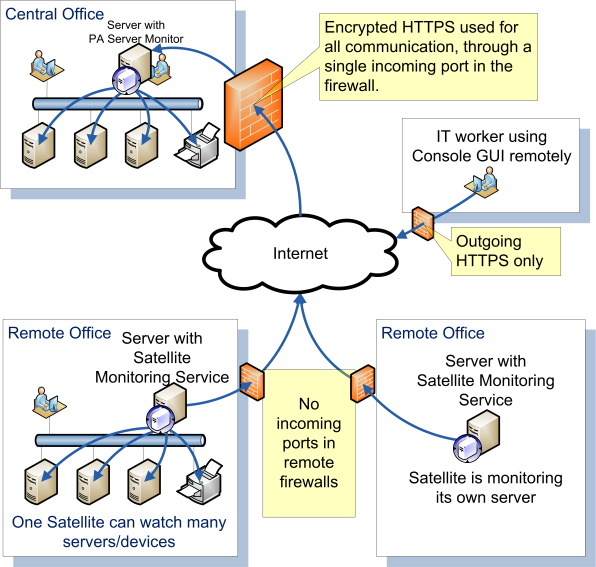
Free and Secure Remote Access? Sort of …
Recently, GoToMyPC forced all customers to reset their passwords. They were not hacked, but rather saw that hackers were attempting to access their customers’ computers using credentials that had been hacked from other places. This seems like a good opportunity to show off how PA Server Monitor can allow remote access in a completely […]
-

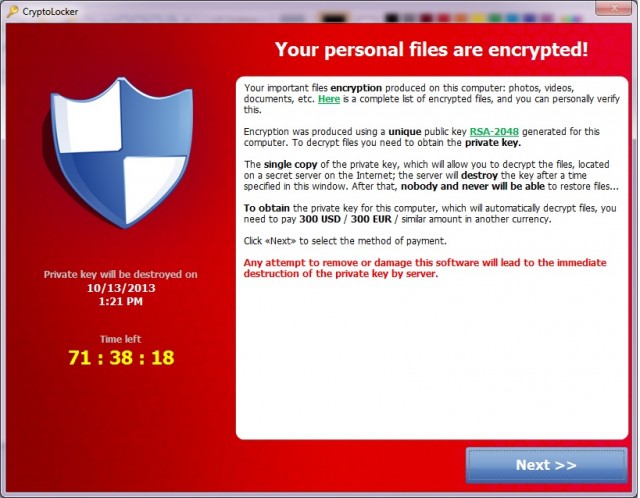
What is Cryptolocker Ransomware?
Cryptolocker is a well known malware (software that does harm) of a particular variety: ransomware. Some malware (like computer viruses) delete and destroy. The hackers that create ransomware have other motivations: money. Ransomware Ransomware does something to your computer, and then demands a ransom payment to get your computer back to the way it used […]
-
Early Detection and Prevention of CryptoLocker
In case you haven’t heard, CryptoLocker is a popular form of the ransomware malware that encrypts your files and then holds them hostage. Generally you have to pay to get them decrypted. If you have a backup of all of your data, you might be able to avoid the payment. If you have a backup… […]
-
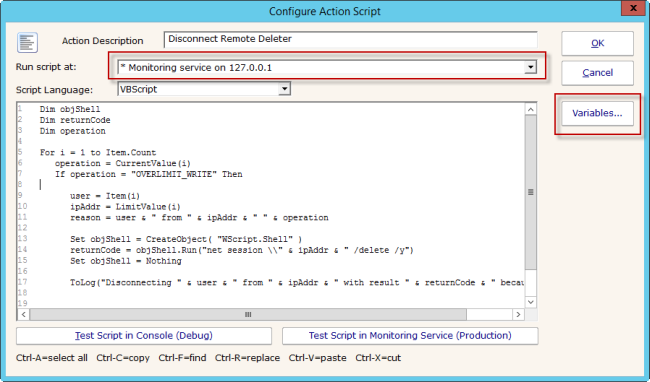
Early Detection and Prevention of CryptoLocker – The Response Scripts
In the previous post, I mentioned a couple of ways customers are working on detecting CryptoLocker attacks. In this post, I’ll share a few scripts they use in response. Ideally, you could quarantine the user’s computer from where the attack is coming from. In practice, that can be tricky. Note that these responses could be […]
-
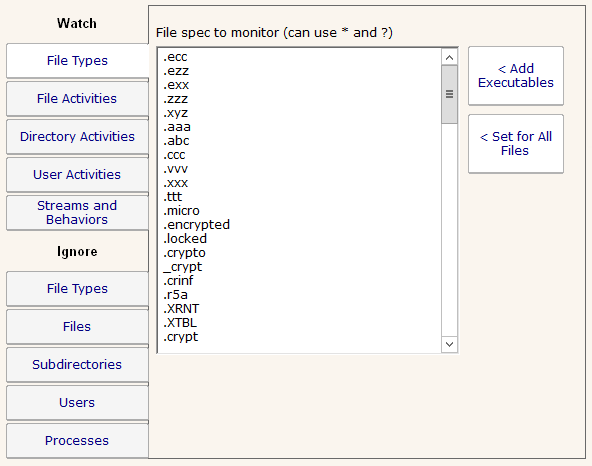
Cryptolocker File Extension List
There is a thread on Reddit that lists many known Cryptolocker file extensions (both the extension that the newly-encrypted file gets, and the ransom note file). A number of customers have asked to be able to more easily paste this list of file names into the list of file types to watch, which is […]
-

Best Practices for Monitoring Windows Logins
Enterprise network administrators usually implement some security and access control measures over standard user accounts, but may neglect service accounts, which become vulnerable targets. As proof against threats from malicious users inside or outside the enterprise – and to comply with regulatory authorities – it’s essential to keep a close eye on what’s […]
-

Best Practices for Monitoring Microsoft IIS Web Server
If you’re working on a Microsoft Windows NT or 2000 platform, chances are you’ll be using Microsoft Internet Information Services (IIS) to build and administer your Web site, search engine, databases, and related applications. This guide will help you monitor and optimise your working environment. What is Microsoft IIS Web Server? Formerly known as Internet […]