Category: Windows
-

The Best Windows Server Back-up Software
Historically, businesses have taken a somewhat lackadaisical approach to backing-up data. These days, while the cloud has allowed for an easier transition into data protection, sadly, many businesses still fail when it comes to backing up daily. In fact, a survey carried out this year found that a huge 53% of SMEs fail to carry…
-

What the Slump in Server Sales means to the Industry
According to a recent press release issued by IDC (International Data Corporation), the American IT market research specialist, global factory output of servers fell for the 3rd quarter of 2013 to $12.1 billion. This represents a 3.7% downturn when compared to the same period 12 months ago. It is the 3rd consecutive quarter that output…
-
Configuring a Public Key Infrastructure-Pt. 2
Part 2, Continued from “How to Configure a Public Key Infrastructure on a Windows Server – Part 1” Enable the policy and check the Renew expired certificates, update pending certificates and remove revoked certificates and update certificates that use certificate templates check-boxes: Now we have to configure certificate templates for auto-enrollment. Open the Certification Authority…
-
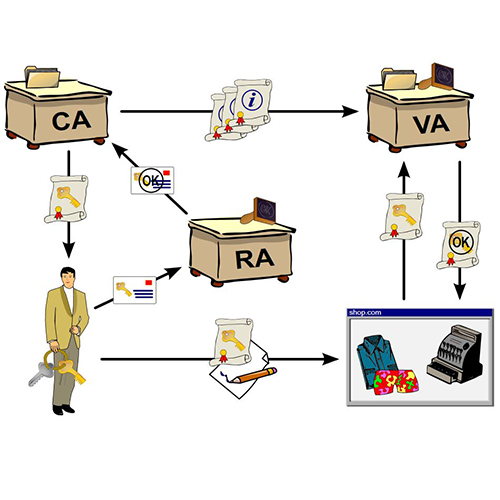
How to configure Public Key Infrastructures
In today’s article we will discuss implementing a PKI (Public Key Infrastructure) on a Windows Server 2008. The PKI will be used to authenticate wireless users. Note that the steps indicated here can also be applied to Windows Server 2012 versions. Before proceeding to the actual practice example, we’ll have to get acquainted with the…
-

3 Signs that Your Server Needs Upgrading
A company server failing can be disastrous, especially if it’s a web server and one that generates sales for the company, but it’s equally damaging if it’s an intranet server, as the cost to the business could prove to be massive. Server failure can lead to downtime for the entire business; if employees can’t access…
-
Why Choose a Data Center to Host your Servers? Part 2
Code Project Cont’d from Why Choose a Data Center to Host your Servers? Quality of Service Companies do not often upgrade their server hardware and this means that most businesses are seldom running the latest equipment, or utilizing cutting edge technology. DCs must use current, quality hardware in order to stay competitive. So a virtual…
-

Why Choose a Data Center to Host your Servers?
More businesses than ever before are now deciding to use Data Centers (DCs) to host their servers. Servers are crucial pieces of equipment. They are the heart of any business’s computer network, often loaded with unique, custom software and programs, and holding sensitive and critical data that a business needs in order to operate. So…
-
Dell PowerEdge 2950: Quieting the Loud Fans! Part 2
Cont’d from Dell PowerEdge 2950 Server: Quieting the Loud Fans! When you have successfully placed the shrink tubes and soldered all the wires together, you should have something similar to the picture below now. You are now ready to fire up the grill lighter and shrink the tubes in place. Heating…
-
An Overview of the New Windows 8 Enterprise Edition – Part 2
Cont’d from “An Overview of the New Windows 8 Enterprise Edition – Part 1” Faster Start-up This is something that will be welcomed by both users and employers alike. All previous versions of Windows take a seemingly long time to boot-up. It results in staff being unoccupied and bored, and to the employer, when multiplied…
-
3 Signs Your Web Server’s Security has been Compromised – Part 2
Code Project Cont’d from “3 Signs that your Web Server’s Security has been Compromised” #2: Check-out the Admin Interfaces Most web applications have some sort of administrative interface. These can be used as an ideal way of allowing hackers into your system. Hackers are often able to manipulate any inherent weaknesses when it comes to…