Category: Technical
-

WiFi Security: What You Should Know
Okay. So, you’re on the road. And you suddenly remember that vital email you neglected to send, before leaving the office. Or you get an urge to post that selfie you just took to your Instagram account. Laptop or mobile device at the ready, you connect to the Web using the free service at the […]
-

A Brief History of Linux
Open source software is no longer the exclusive preserve of developers and tech-heads looking to become the next Bill Gates while simultaneously shunning Windows. It’s popular with the masses now, too – largely because it’s free. One of the driving forces behind its widespread adoption has been the continued success of Linux. This article will […]
-

SSL And Beyond, Part 2: Compatibility & Deployment Across the Board
In our first installment we discussed the origins and development of the Secure Sockets Layer (SSL) protocol and considered its role in providing secure internet connections through encryption and the use of digital certificates. In this article, we’ll go further into the use case to discuss how applications are deemed compatible with SSL, and how […]
-

Hyper-V features Introduced in Windows Server 2012
As most of you already know, Hyper-V is the virtualization product that is shipped with Windows Server Editions. Microsoft has continuously added new features it and has really enhanced its capabilities. With Windows Server 2012 Edition, Microsoft introduced multiple features that allows further configuration to your virtualization environment. In this article we will discuss about […]
-

A Brief History of Microsoft Windows
In 2015, it is hard to imagine a world without Microsoft Windows. As of May 2015, Windows operating systems account for over 90% of the desktop operating system market share, with Windows 7 being the most popular single operating system at 57.76% of the market. While Mac OS and Linux have found increasing popularity over […]
-

SSL and Beyond, Part 1: History, and Development
Online communications and e-commerce are fast replacing more traditional methods. So there’s a real need for data to be moved around through secure channels. That’s where protocols like the Secure Sockets Layer or SSL have a part to play. This series will consider the evolution of SSL, its current deployment, and options for the future. […]
-
Converting a Windows Server with GUI to Server Core and vice versa
Windows Server 2012 comes with a couple of new features that can be used to make your life as a System Administrator much better. One of these cool features is the ability to convert a server with full installation into a core edition and vice versa. You can perform this action because each full installation […]
-
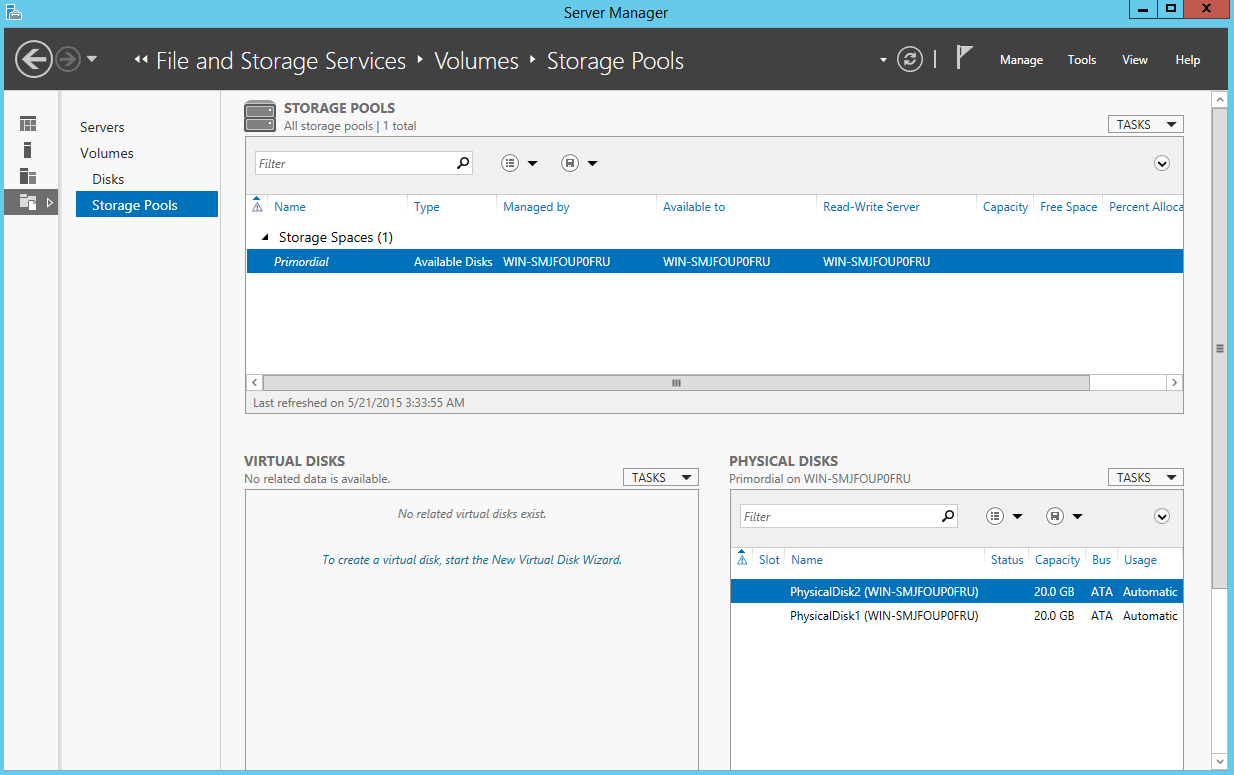
How to Create Local Storage with Windows Server 2012
We’ve talked previously about some of the features newly introduced with Windows Server 2012. In this article we’ll discuss Storage Spaces, a feature that allows you to provision storage to remove servers by creating storage pools. With Storage Spaces you can utilize physical inexpensive disks that once configured react just like a SAN (storage area […]
-

Types of Network Monitoring Applications
Information security is a big ticket issue for organizations, as sensitive data represents a gold mine for cyber criminals. Data breaches cost companies an average of $3.5 million in 2014, according to an IBM study. Another major risk for companies is network downtime. This costs companies up to $5,600 per minute, according to a Gartner survey. There’s no […]
-

The Evolution of Operating Systems
Fast and efficient digital transactions are taken for granted, these days – whether they be over the counter purchases, a hiccup-free database search, or a smooth download from the Web. None of this would be possible if the operating environments for our computers hadn’t gone through radical changes since their inception. Operating, On…? Concealing the […]