Category: Technical
-

Best Tips for Managing an MS SQL Server
With compatibility issues arising between various versions of the platform, and the emergence and evolution of new features and tools, managing a Microsoft (MS) SQL Server and its associated database functions may sometimes feel like playing a game of “Catch Up.” We’ve assembled some outline tips and best practices, to assist you. Full details…
-

Installing VSphere Hypervisor (VMWare ESXi 6.5) on an Intel NUC
We test our software a lot, and it helps to have a large network. We don’t have thousands of servers like many customers, but we can simulate a large network which gives us better real-world testing. It’s time to expand our environment again, but we didn’t want to setup another large server for VMs that ultimately…
-

Monitor (Failed) User Logins in Active Directory
Everyone knows you need to protect against hackers. How do you protect your computers from hackers? One way is to monitor for lots of failed login attempts. But how do you do that? With Windows, you watch the Security Event Log – there are many, many events related to users logging in, failing to…
-

Reducing Downtime While Backing Up AWS EC2 Instances
We’re big fans of AWS and use several of its services. One service we use is EC2 – it costs much less than having a dedicated server and still gives you full control of the server. One issue is being sure we can bring the server back up in case it crashes, or the…
-
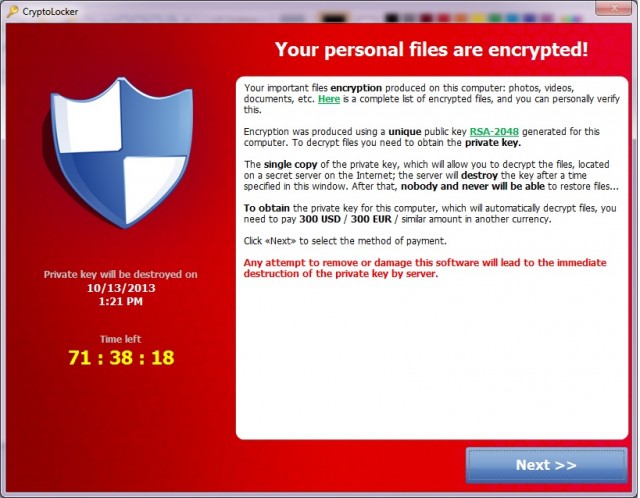
Early Detection and Prevention of CryptoLocker
In case you haven’t heard, CryptoLocker is a popular form of the ransomware malware that encrypts your files and then holds them hostage. Generally you have to pay to get them decrypted. If you have a backup of all of your data, you might be able to avoid the payment. If you have a backup……
-
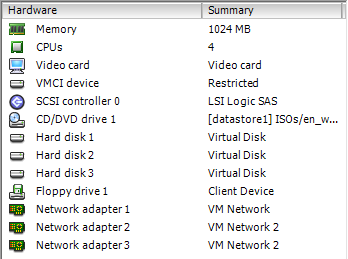
Simulating a Large Network
We live, eat, breathe and love monitoring here at Power Admin. So we’re always looking for ways to improve. One way is to scale our software to handle ever increasing loads. Some of our larger customers (the largest anti-virus and computer security software company in America which starts with ‘Sym’ and ends with…
-
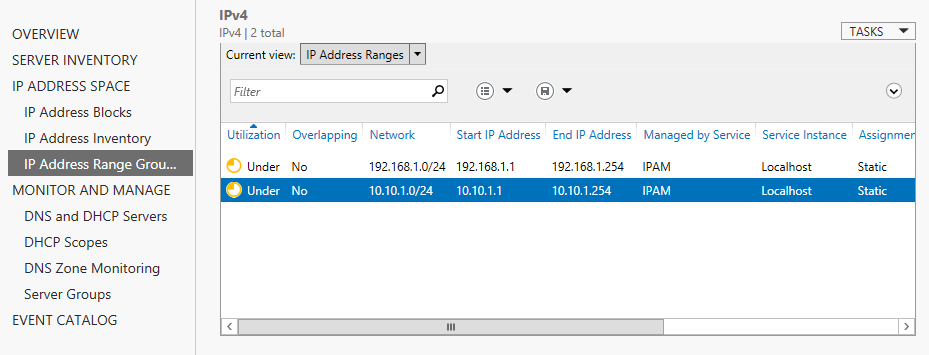
Configuring IPAM IP address spaces
In our previous IPAM article we’ve started discussing about this brand new technology that was introduced with the release of Windows Server 2012. We’ve seen how to install and configure IPAM and we’ve also managed to add a server to our IPAM database. In this article I want to further dive into the features that…
-

7 Simple Steps to Configure IPAM in Windows Server 2012
IP address management (IPAM) is a new feature introduced in Windows Server 2012 that allows you to configure, manage and have a general overview of the network’s IP addresses and ranges. With IPAM, you can search for desired IP addresses and ranges, manage and configure DHCP scopes and DNS entries, view the status of your…
-
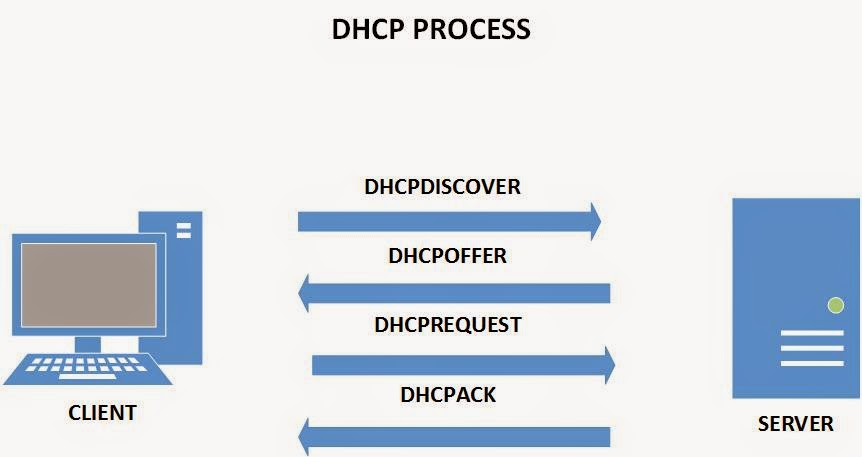
How to install and configure a DHCP Server on a Linux machine – Part 2
Hi folks, In the previous article we’ve configured a CentOS machine and installed the DHCP package. We’ve then created a sample configuration file for our machine, but we haven’t finished deploying our DHCP server yet. In this article we’ll finish our configuration and hopefully, we’ll be able to obtain an IP address lease from our DHCP machine.…
-
Scale-Out Windows File Servers
Scale-Out File Server is a new feature introduced in Windows Server 2012 Edition which allows you to deploy a File Server with advanced functionalities. If you’ve worked with previous Windows Server Editions you probably know that you can configure a File Server for high availability within a failover cluster. I’ve configured previously this role in…