Category: Technical
-
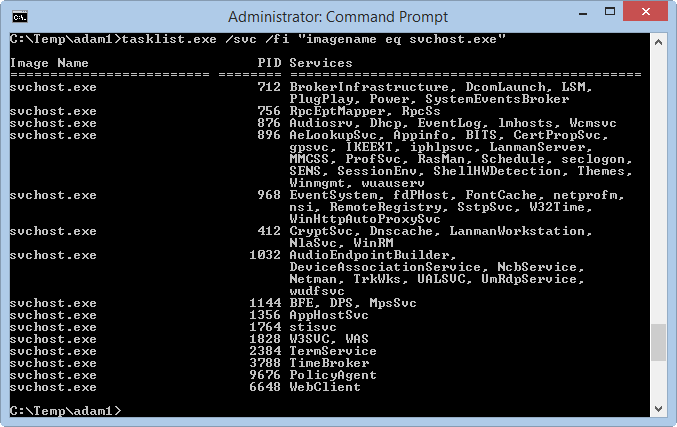
Windows 2003 and High CPU Usage in Svchost
Windows 2003 is getting a bit long in the tooth, but we’ve got a number of customers that are still happily using it, and for good reason — it’s a solid work horse of an OS. We’ve recently come upon an issue where some of our 2003 servers in the lab were pegging the CPU…
-

Building OpenSSL with Visual Studio 2012 for 32- or 64-bit
For our programmer (dev/ops) friends, we thought we’d share a little about building OpenSSL. There are a lot of examples online, but we kept finding they had little glitches, not quite complete, etc. So here is how we built it: You need Perl installed. ActiveState’s free community Perl install is just fine. First, you need to…
-

SHA-1 Hashing Algorithm & Windows 2003
In 2012, the U.S. National Institute of Standards and Technology (NIST) indicated that the SHA-1 hashing algorithm should no longer be used by federal agencies. Our products use self-signed SSL certificates by default (you can replace that with your own certificate), and SHA-1 is used as the signature algorithm. We started researching moving to SHA-2…
-

How to Monitor MS SQL Server
This will be the third in our blog series about monitoring. The first covered monitoring IIS and the second, monitoring ASP.NET. Please take a look at these first to get some basic information about how to monitor different Windows products. In today’s article we will focus on how to use monitoring software to visualize, troubleshoot…
-

How to Monitor ASP.NET
Last week we talked about how to monitor IIS. Today we’re going to discuss monitoring ASP.NET. We’ll cover a number of things including: the main implications of monitoring ASP.net, the most important performance counters to look for, performance counter values that should be measured and services dependent on ASP.net that should be monitored. If you…
-

How to Monitor IIS
This will be the first in a series of three blog posts on monitoring. In this article we’ll discuss monitoring Internet Information Services (IIS), the web hosting platform available in Windows Server editions. IIS is very popular in part because it provides such a compact service with lots of features and configurations. Most enterprises that…
-
PA Server Monitor: Download to Monitoring in Under 8 Minutes!
Check out our quick tutorial on how to download, install, configure, and get alerts and reports from PA Server Monitor™ software. If you haven’t downloaded our 30 day free trial yet, just grab a copy of PA Server Monitor, and follow along with the video below to get it set up quickly. It’s a full…
-

Why Is Network Security Important?
As the internet evolves and computer networks become bigger and bigger, network security has become one of the most important factors for companies to consider. Big enterprises like Microsoft are designing and building software products that need to be protected against foreign attacks. By increasing network security, you decrease the chance of privacy spoofing, identity…
-

Perfect Forward Security and SSL Encryption
Michael Horowitz wrote a great article at Computer World entitled Perfect Forward Secrecy can block the NSA from secure web pages, but no one uses it. The tl;dr – encrypted HTTPS communications can be saved by Big Brother, and if the private key is broken at some time in the future, the saved communications can…
-

What is IPv6 and an IPv6 Address?
You are probably aware that today’s communications rely very heavily on the Internet Protocol. An IP address is a unique identifier for each machine connected to the Internet. With the ever growing size of the Internet, the demand for IP addresses increased drastically. Today’s IPv4 supports 2 to the power of 32 addresses […]