Category: Tech
-

Using Threat Intelligence Services to Enhance Security
Trying to recover from a cyber-assault or serious data breach can be a stressful and expensive affair. A far better approach is to make sure that your business is safe from such catastrophes before they occur – or at the very least, capable of staging a swift recovery in the event that disaster does strike.…
-

Power Admin Network Technology Scholarship
Power Admin is delighted to announce the Power Admin Network Technology Scholarship. The program will award $2000 to a diligent student each year. The scholarship is intended to help young students afford the increasing cost of tuition and help them along the road to a future career in the networking technology/IT field. Before you…
-
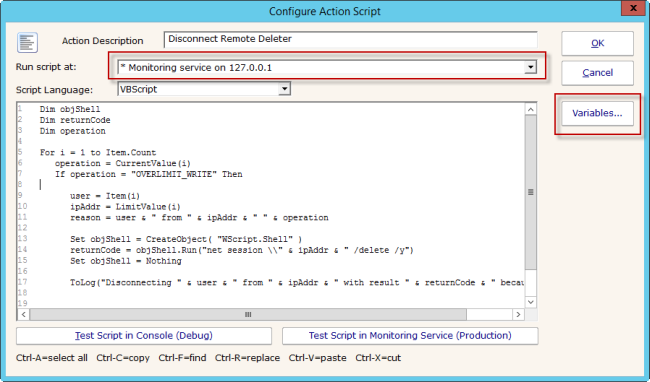
Early Detection and Prevention of CryptoLocker – The Response Scripts
In the previous post, I mentioned a couple of ways customers are working on detecting CryptoLocker attacks. In this post, I’ll share a few scripts they use in response. Ideally, you could quarantine the user’s computer from where the attack is coming from. In practice, that can be tricky. Note that these responses could be…
-

Enterprise Applications of Artificial Intelligence
Much of our conception of Artificial Intelligence or AI has been shaped by popular movies: from the homicidal Red Queen of “Resident Evil”, to the J.A.R.V.I.S. operating system / virtual butler that provides logistical support to “Iron Man”. Extremely advanced intelligence and – in some cases – living machine consciousness. We’re not quite…
-
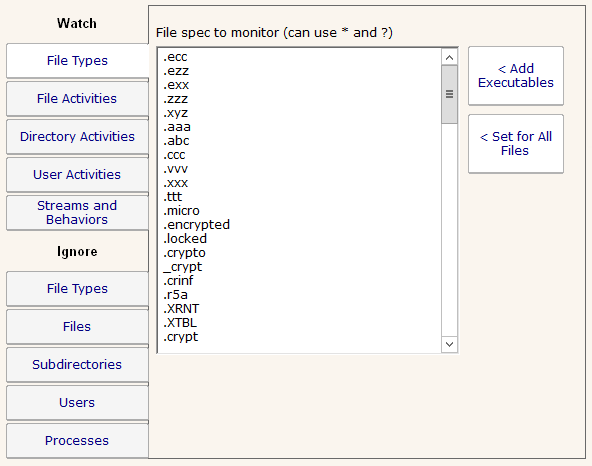
Cryptolocker File Extension List
There is a thread on Reddit that lists many known Cryptolocker file extensions (both the extension that the newly-encrypted file gets, and the ransom note file). A number of customers have asked to be able to more easily paste this list of file names into the list of file types to watch, which is…
-

51 DevOps Influencers to Start Following Today
While the objectives of DevOps are to stop wasting time and money on IT projects that become slow, unwieldy and incredibly bureaucratic, the whole concept is really about people- perhaps more so than technology. It’s probably for this very reason that a community of evangelists and advocates has grown and become instrumental in sharing…
-

What is a Private Cloud?
According to the National Institute for Standards in Technology (NIST), cloud computing as a whole provides a measured and on-demand self-service, with pooled resources, broad network access, and the rapid and elastic scaling of resources. And it’s on the rise – particularly with corporate clients. But there’s still some confusion about its various…
-

How Has Mobile Technology Impacted Data Security?
Mobile technology has fundamentally changed the way day to day business is carried out – of this there is little doubt. No longer is business restricted to the place of work or normal working hours. Conference calls can be made from almost anywhere, emails can be sent and received, and files can be shared with…
-

Best Practices for Monitoring Oracle Database
As administrators, the responsibility for keeping a database running smoothly extends to satisfying not only the demands of users but also the requirements of senior management and the enterprise as a whole. In an Oracle environment, this requires setting up an infrastructure for monitoring the system that hinges on the objectives laid down by…
-

Best Practices for Monitoring Microsoft Sharepoint
With “collaboration” a watchword for much of business practice today, and online platforms providing the environment in which it takes place, it’s essential to ensure that your working data is available and secure. For Windows users especially, Microsoft SharePoint is the platform of choice. This guide will help in monitoring and maintaining your SharePoint…