Category: Tech
-

Intent-Based Networking
The software-defined approach to network management and implementation relies on the creation of an abstraction layer, to provide a virtual overlay on the physical infrastructure of servers, switches, routers, and wireless access points. Historically, the creation and management of these virtual network layers has been accomplished through a combination of virtual Local Area Networks […]
-
Comparisons of Azure vs Amazon AWS
Given the advantages offered in expanded infrastructure, increased computing power and data storage capacity, flexibility, time-saving, and decreased management and maintenance overheads, it’s easy to understand why growing numbers of enterprises are committing their resources to some form of cloud-based service or platform. Mention the words “cloud platform” in a commercial context, and two […]
-
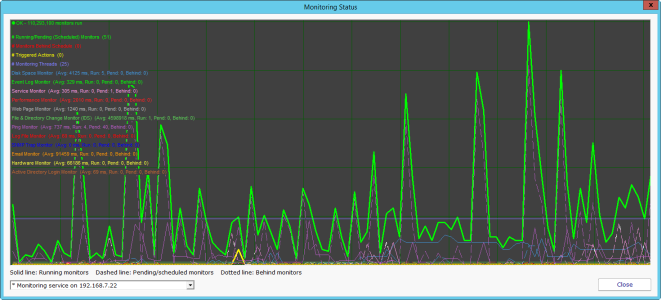
See Real-Time Monitoring Load
Did you know you can double-click the heartbeat chart in the upper-right corner of the Console to see an expanded version of that chart? The expanded version shows the various monitor types and which ones are currently running, which monitor types are behind, etc. As of version 7.4 it’s also possible to see this […]
-

GDPR and the UK Data Protection Bill
The GDPR and UK Data Protection Bill have some similar language to the PCI DSS involving keeping track of data and who/what process is accessing data. Specifically, Article 30 indicates data processors “shall maintain a record of all categories of processing activities“. Customers are beginning to turn to PA File Sight for help with this. […]
-

Backup Strategies For Data Centers
Even for the smallest scale enterprise, the practice of making regular, clean, and tested backups of essential information is fundamental to ensuring business continuity, data integrity, and security. When an organization is of a size that warrants the use of a full-blown data center, this ups the game considerably. After all, the information being […]
-

Is Cybercrime on the increase?
In recent months, a significant amount of media coverage has been given to the plight of high-profile organisations falling prey to cyber-attacks of rapidly increasing sophistication and severity. With this in mind, you would be forgiven for thinking that there is something of an epidemic in cyber-crime at present. But is this really the case, […]
-

7 reasons to upgrade to Windows 10
Not upgraded to Windows 10 yet, and unsure whether you should make the switch or not? Here we’ll examine the reasons why now is the time to consider switching up, whilst also revealing some of the pitfalls that may make you think twice. There are many good reasons why you should upgrade, our top […]
-

Installing VSphere Hypervisor (VMWare ESXi 6.5) on an Intel NUC
We test our software a lot, and it helps to have a large network. We don’t have thousands of servers like many customers, but we can simulate a large network which gives us better real-world testing. It’s time to expand our environment again, but we didn’t want to setup another large server for VMs that ultimately […]
-

The DRaaS Option
When natural, circumstantial, or man-made disasters strike, large corporations with considerable financial, physical, and human resources clearly have the edge over their smaller rivals when it comes to maintaining services, preserving application and network availability to subscribers and in-house users, and preserving the integrity of their systems and data. But there’s an option available […]
-

Monitor (Failed) User Logins in Active Directory
Everyone knows you need to protect against hackers. How do you protect your computers from hackers? One way is to monitor for lots of failed login attempts. But how do you do that? With Windows, you watch the Security Event Log – there are many, many events related to users logging in, failing to […]