Category: Tech
-

How To Maximize On Your Usage Of Awk
Abbreviated from the names of its developers – Aho, Weinberger, and Kernighan – Awk is a scripting language used in Unix or Linux environments for manipulating data and generating reports. The awk command programming language requires no compiling, and allows the user to employ variables, numeric functions, string functions, and logical operators. In this […]
-

How To Decommission A Data Center
The potential for disrupting business is much greater when you decommission a data center than if you’re constructing one. The process involves a lot more than just shutting down servers, turning off switches, and dismantling storage racks. In this article, we’ll consider some of the specifics and best practices required to achieve a smooth decommissioning […]
-
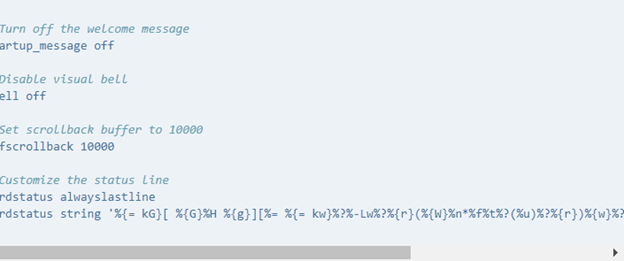
How To Get The Most Out Of The Linux Screen Command
If you’re logging onto a service or running remote command line operations over a network link via the Secure Shell (SSH) protocol, the last thing you need is for your session to be cut off by a faulty connection. This scenario is all too common – but for Linux users, the Screen utility can prevent […]
-
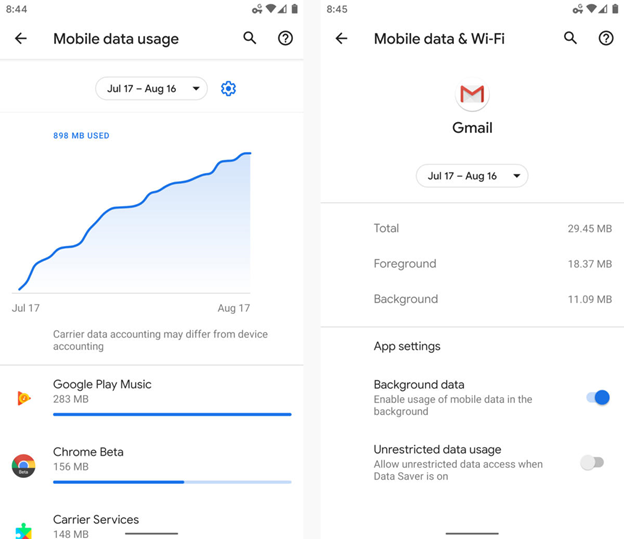
How To Cut Down Your Data Usage On Android
If you’re an Android user, relying on data from your cellular provider is one way of avoiding the risks of free public Wi-Fi – especially if you don’t have the tools or services necessary to give you full protection. Android also has a huge and widely varied user base distributed across the globe. […]
-

How To Choose A Database For Your Application
Software of all kinds requires information to do its work. At the back end of most programs you’ll usually find some form of database, which has been created or selected and configured to run specifically with that application. In creating that database or making a selection from the wide range of products available, there […]
-

Building Business with Cybersecurity
Cybersecurity is a hot topic. With high profile breaches making headlines on almost a monthly basis, combined with a far more restrictive regulatory environment, the need to responsibly protect your customers’ data has never been felt more keenly. It is estimated that a business is subjected to a ransomware attack every 14 seconds, predicted […]
-
Android 10 – Everything You Need to Know
If you own a Google Pixel smartphone (or one of a couple of other models) Android’s latest update is finally here. If you own another model of Android smartphone then you’ll have to wait a little longer, but that’s nom de rigueur for the operating system. Dubbed Android 10, the new update has abandoned […]
-
8 Top Robotic Process Automation (RPA) Tools
By Des Nnochiri Robotic process automation, or RPA, promises to increase efficiency and improve work rates at reduced cost to the enterprise. In this article, we’ve assembled eight of the top RPA tools currently on the market. Of course, there are considerations to bear in mind before implementing this emerging technology. What Is […]
-
Is Blockchain a Permanent Fixture in the IT Industry?
By Des Nnochiri In essence, the nature of business comes down to different companies exchanging value with supplier, partners, and customers. By “value”, we mean goods, services, money, and data. This is the fundamental basis of any business and it has to do this effectively in order to make a profit and survive. […]
-

Comparing Skype for Business and Zoom
By Des Nnochiri As globalization has created workspaces far wider than the average office, video conferencing software has become an everyday tool for many business owners, employers, and employees. Using software that facilitates live video conferences between two or more parties via video, audio, and text while also allowing sharing and collaborating on files […]