Category: Tech
-

An Overview of the New Windows 8 Enterprise Edition
Not since the launch of the Windows Vista operating system has there been so much negativity about the latest upgrade of Windows for consumers. But is it really justified, or is it simply misinformation and/or the lack of information that has driven large swathes of the business community to avoid it thus far? Setting…
-
Tips 8-12: How to Optimize and Speed Up Windows 7 Performance
Cont’d from… “Top 12 Tips: How to Optimize and Speed Up Windows 7 Performance” #8. Uninstall any unwanted program I recommend that you uninstall any unused programs from your computer. By doing this, registry keys are cleaned, hard disk space is increased, running processes are reduced and overall computer’s performance is increased. You can uninstall software…
-

Choosing a Network Monitoring Solution – TechRepublic
Take a look at our write up in TechRepublic, featuring PA Server Monitor, and how some of our customers have used it. Considerations for Choosing a Network Monitoring Solution It talks about why server monitoring is good for business, and choosing between “paid” or “rented” software solutions. A big thanks to Nick Hardiman at TechRepublic…
-
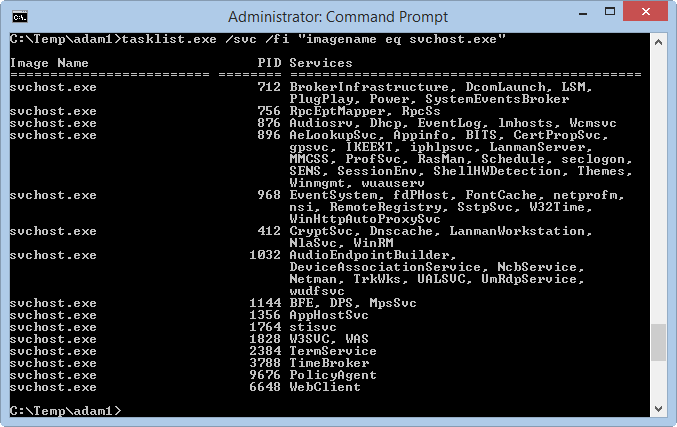
Windows 2003 and High CPU Usage in Svchost
Windows 2003 is getting a bit long in the tooth, but we’ve got a number of customers that are still happily using it, and for good reason — it’s a solid work horse of an OS. We’ve recently come upon an issue where some of our 2003 servers in the lab were pegging the CPU…
-

SHA-1 Hashing Algorithm & Windows 2003
In 2012, the U.S. National Institute of Standards and Technology (NIST) indicated that the SHA-1 hashing algorithm should no longer be used by federal agencies. Our products use self-signed SSL certificates by default (you can replace that with your own certificate), and SHA-1 is used as the signature algorithm. We started researching moving to SHA-2…
-

How to Monitor ASP.NET
Last week we talked about how to monitor IIS. Today we’re going to discuss monitoring ASP.NET. We’ll cover a number of things including: the main implications of monitoring ASP.net, the most important performance counters to look for, performance counter values that should be measured and services dependent on ASP.net that should be monitored. If you…
-

How to Monitor IIS
This will be the first in a series of three blog posts on monitoring. In this article we’ll discuss monitoring Internet Information Services (IIS), the web hosting platform available in Windows Server editions. IIS is very popular in part because it provides such a compact service with lots of features and configurations. Most enterprises that…
-

Why Is Network Security Important?
As the internet evolves and computer networks become bigger and bigger, network security has become one of the most important factors for companies to consider. Big enterprises like Microsoft are designing and building software products that need to be protected against foreign attacks. By increasing network security, you decrease the chance of privacy spoofing, identity…
-

Coolest Photo of PA Server Monitor in Action…
Ever wonder how others might be using PA Server Monitor? We sure do! And it was very kind of one of our customers to share a picuture of our software in action. We won’t say who it was, but we can say it’s a Network Operations Center in Brazil for a high-profile, world-wide soccer organization.…
-

What is IPv6 and an IPv6 Address?
You are probably aware that today’s communications rely very heavily on the Internet Protocol. An IP address is a unique identifier for each machine connected to the Internet. With the ever growing size of the Internet, the demand for IP addresses increased drastically. Today’s IPv4 supports 2 to the power of 32 addresses […]