Category: PC Security
-

What is HIPAA Compliance?
HIPAA stands for the Healthcare Insurance Portability and Accountability Act of 1996. This specifies laws for the protection and use of Personal (or Protected) Health Information (PHI) – essentially, your medical record. HIPAA sets the standard for protecting sensitive patient data. The Administrative Simplification provisions of the Act (HIPAA, Title II) require the U.S. Department […]
-

NAP Enforcement (Network Access Protection)
NAP or Network Access Protection is a Windows Server security mechanism which enables you to control how computers gain access to network resources. The main functionality of NAP is to verify and ensure that only healthy computers will be marked as compliant and will receive network access. In this article we will talk about some […]
-

2014 Security Threats & the Impact of Cybercrime
The cost of cybercrime, mobile threats on the rise, Zero Day threats…what every business needs to know.
-

Keeping cybercrime out – tips on network security
Threats to network security are greater today than they’ve ever been. From botnets to spies, everyone’s trying to get access to your system and its data. Among the biggest threats to networks are basic spyware and adware, denial of service attacks that can choke entire systems and bring them down, direct attacks by hackers and […]
-

How to use Windows Firewall to Authorize Connections
In this article I will show you how to use Windows Firewall to authorize connections before data can be sent between devices. Authorization offers you an extra security layer and should be used whenever possible. There are services or applications that include authorization rules so that only allowed users/computers can connect to certain network resources. […]
-

The Best Windows Server Back-up Software
Historically, businesses have taken a somewhat lackadaisical approach to backing-up data. These days, while the cloud has allowed for an easier transition into data protection, sadly, many businesses still fail when it comes to backing up daily. In fact, a survey carried out this year found that a huge 53% of SMEs fail to carry […]
-

Infographic – Is Your Password Keeping You Safe?
Important possessions are often protected with a lock, chains, and welded metal. But many people protect some of their most valuable belongings with only one word. A password. How important is a password? What kinds of things do they protect? History has some interesting cases of passwords, especially considering why they were invented in the […]
-

Is your Network Being Monitored by the NSA?
This year has proved to be something of an embarrassment for the US and UK governments, both having been caught red-handing spying on their own, and other country’s, citizens by whistle-blower Edward Snowden. Of course, it’s not the government themselves so to speak, but the agencies the US National Security Association (NSA) and UK Government […]
-
Configuring a Public Key Infrastructure-Pt. 2
Part 2, Continued from “How to Configure a Public Key Infrastructure on a Windows Server – Part 1” Enable the policy and check the Renew expired certificates, update pending certificates and remove revoked certificates and update certificates that use certificate templates check-boxes: Now we have to configure certificate templates for auto-enrollment. Open the Certification Authority […]
-
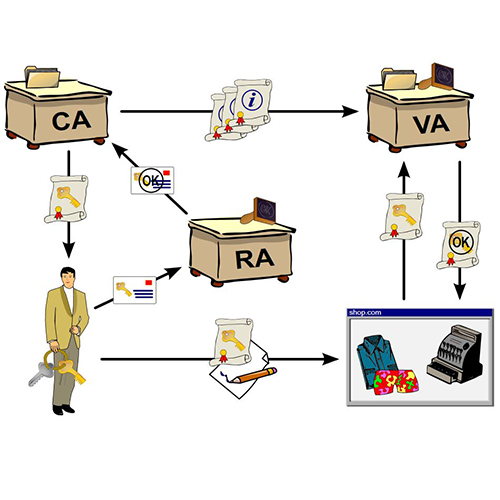
How to configure Public Key Infrastructures
In today’s article we will discuss implementing a PKI (Public Key Infrastructure) on a Windows Server 2008. The PKI will be used to authenticate wireless users. Note that the steps indicated here can also be applied to Windows Server 2012 versions. Before proceeding to the actual practice example, we’ll have to get acquainted with the […]