Category: PC Security
-

How to Prepare for a DDoS Attack
With much of today’s commercial activity conducted via the Internet, it’s no wonder that corporate entities find themselves the target of assault by online intruders. Cyber-attacks are now an accepted part of life – and it’s up to administrators and security officers to establish how best to prepare and defend their organisations against them.…
-

How Has Mobile Technology Impacted Data Security?
Mobile technology has fundamentally changed the way day to day business is carried out – of this there is little doubt. No longer is business restricted to the place of work or normal working hours. Conference calls can be made from almost anywhere, emails can be sent and received, and files can be shared with…
-
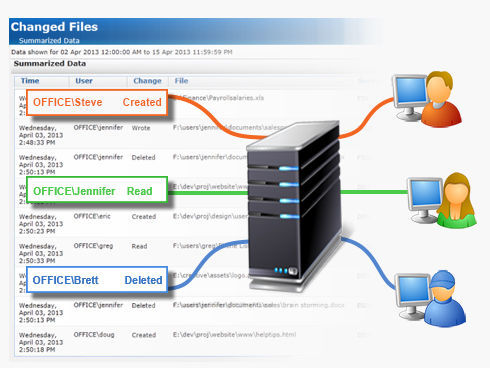
PA File Sight version 6 Beta!
PA File Sight version 6 is now in Beta! For those not yet in the know, PA File Sight tracks who is accessing files on a Windows server. Lots of software can tell you who created or saved a file. Almost no products can tell you who is reading from a while, or who deleted…
-

WiFi Security: What You Should Know
Okay. So, you’re on the road. And you suddenly remember that vital email you neglected to send, before leaving the office. Or you get an urge to post that selfie you just took to your Instagram account. Laptop or mobile device at the ready, you connect to the Web using the free service at the…
-

SSL And Beyond, Part 2: Compatibility & Deployment Across the Board
In our first installment we discussed the origins and development of the Secure Sockets Layer (SSL) protocol and considered its role in providing secure internet connections through encryption and the use of digital certificates. In this article, we’ll go further into the use case to discuss how applications are deemed compatible with SSL, and how…
-

SSL and Beyond, Part 1: History, and Development
Online communications and e-commerce are fast replacing more traditional methods. So there’s a real need for data to be moved around through secure channels. That’s where protocols like the Secure Sockets Layer or SSL have a part to play. This series will consider the evolution of SSL, its current deployment, and options for the future.…
-

Types of Network Monitoring Applications
Information security is a big ticket issue for organizations, as sensitive data represents a gold mine for cyber criminals. Data breaches cost companies an average of $3.5 million in 2014, according to an IBM study. Another major risk for companies is network downtime. This costs companies up to $5,600 per minute, according to a Gartner survey. There’s no…
-

Top Priorities for IT in 2015
As organizations continue the trend of transforming physical processes and business models into digital ones, it’s worth having a look at those issues that will vex or focus the minds of IT divisions and Chief Information Officers (CIOs) in the coming year. Broad Strategic Moves Every year in the US, the National Association of State…
-

LinkedIn Feature: Monitoring in the Cloud Examined
It’s that time again for a brand new, in-depth 3 part article we post on LinkedIn! So, starting today (March 13th 2015), we are posting up a very special extended 3-part feature exclusively on LinkedIn entitled ‘Monitoring in the Cloud’ Cloud computing is very popular right now. That being said, there are definitely some risks…
-

The Top 3 Best Password Managers
There was once a time when all you needed to do was remember your email login password and you could be described as a top-notch password manager yourself. Not so anymore. With today’s business and even personal world taking place almost entirely online, we find ourselves having to remember sometimes literally dozens of passwords. As…