Category: PC Security
-

Using Threat Intelligence Services to Enhance Security
Trying to recover from a cyber-assault or serious data breach can be a stressful and expensive affair. A far better approach is to make sure that your business is safe from such catastrophes before they occur – or at the very least, capable of staging a swift recovery in the event that disaster does strike. […]
-

Unmasking the Imposters, Part 2: Detection and Damage Control
In the first of this two-part security report, we discussed the threat presented to individuals and enterprises by malicious outsiders posing as members of an organisation itself, or representatives of a trusted external institution like a bank or popular online resource. We looked at how these imposters are refining their methods of extracting funds or […]
-

Unmasking the Imposters, Part 1: An Evolving Threat
We’ve come a long way, since the first large-scale outbreaks of advanced fee fraud and email account hacking, back in 1986. In the years to date, cyber-criminals and fraudsters have stepped up their game, considerably – to the point where (in some unfortunate organisations) it’s nearly impossible to distinguish between genuine staff and authorised […]
-
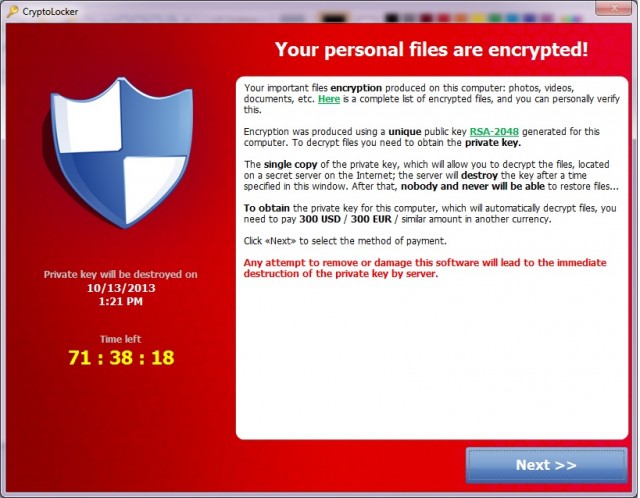
Early Detection and Prevention of CryptoLocker
In case you haven’t heard, CryptoLocker is a popular form of the ransomware malware that encrypts your files and then holds them hostage. Generally you have to pay to get them decrypted. If you have a backup of all of your data, you might be able to avoid the payment. If you have a backup… […]
-
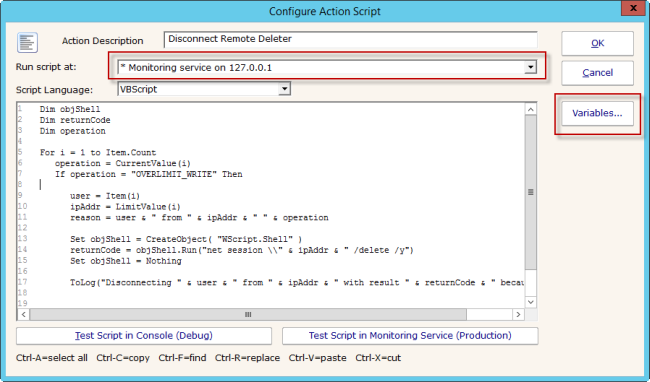
Early Detection and Prevention of CryptoLocker – The Response Scripts
In the previous post, I mentioned a couple of ways customers are working on detecting CryptoLocker attacks. In this post, I’ll share a few scripts they use in response. Ideally, you could quarantine the user’s computer from where the attack is coming from. In practice, that can be tricky. Note that these responses could be […]
-

Maintaining a Secure SDN
As technologies continue to evolve, the nature of IT infrastructure is changing. Virtualisation, hyper-convergence and increased connectivity are presenting fresh opportunities for malicious intruders to gain access to networks. One of the platforms presenting new possibilities to both network administrators and hackers is SDN. What is SDN? A software-defined network or SDN is an […]
-
Making Security an Integral Part of DevOps
In the rush to innovate, steal a jump on the competition, and bring new software products to market, enterprises have embraced the concept of DevOps: the peaceful co-habitation of Development and Operations, for more effective co-operation between the two. But this competitive frenzy often overlooks a vital aspect: security. In this article, we’ll […]
-
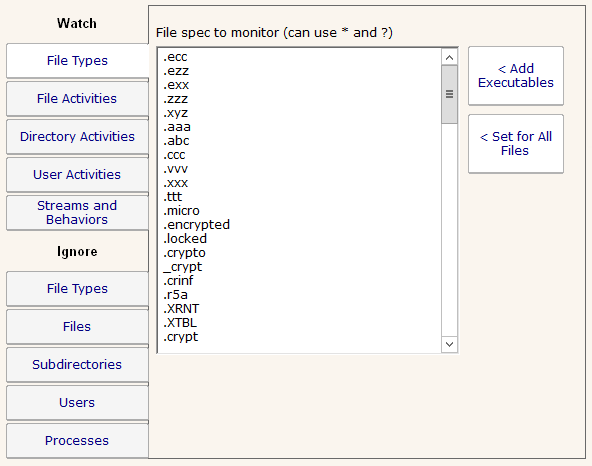
Cryptolocker File Extension List
There is a thread on Reddit that lists many known Cryptolocker file extensions (both the extension that the newly-encrypted file gets, and the ransom note file). A number of customers have asked to be able to more easily paste this list of file names into the list of file types to watch, which is […]
-

Making PCI Compliance Less Stressful
If your business requires you to deal with credit card holders, you’ll have records of your customers’ account details. Both your customers and you will want to know that this information is kept safe, and free from prying eyes. It’s not just good business practice; it’s the law. And complying with this legal […]
-

Your Cyber-Threat Assessment for 2016
The year just past saw several high-profile cyber-attacks hit the news, and brought the whole issue of cyber-security firmly into the spotlight. With the lessons still being learned from 2015 in mind, let’s look ahead to what you should be wary of in the months to come. Home is Where the Hurt Is? “Smart” domestic […]