Category: Monitoring
-
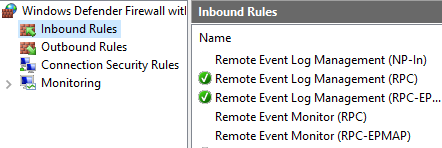
Event Log Monitors Failing? Check Windows Firewall
In the past week or two we have been receiving a lot of email from customers reporting that their Event Log Monitor has suddenly started failing on a number of servers. We don’t have proof, but we’re guessing a recent Windows Update must have disabled the Remote Event Log Management rules. (Edit): Confirmed! Thanks […]
-

What Should You Do When You Receive Event Log Monitor Alerts?
When you are installing PA Server Monitor, you will need to configure what occurs when there are event log monitor alerts. You typically set this up during the initial install. However, it is not uncommon to want to make changes and updates or even add new events to your server monitoring software as you become […]
-

How to Configure PA Server Monitor to Monitor Your Event Logs
Did you know that you could configure PA Server Monitor’s Event Log Monitor feature to monitor one or more of your event logs? The event logs can include standard application, security, and system logs, as well as any custom event logs you want to monitor. With our server monitoring software, you have complete control and […]
-

How Can an IT Server Monitoring Service Improve Your Net Profits?
You might not think that an IT server monitoring service would have an impact on your net profits. IT-related costs often fall under operational expenses. As such, you have better control over these expenses and can look for different ways you can cut costs without affecting results. Before we get to reviewing some of […]
-

How PA Server Monitor Can Monitor CPU Temperature
High CPU temperature is a common issue with laptops and desktops, and it shouldn’t be ignored. If a computer system routinely generates high temps—above 80°C is usually considered undesirable—it can begin experiencing poor system performance. Over time, heat may progressively damage CPU components in addition to causing the system to lock up or shut down. […]
-

Active Directory Security Best Practices Includes Monitoring for Signs of Compromise
Fun Fact: Most types of network and computer compromises could have been discovered much sooner if the organization had enabled proper event log monitoring using an appropriate server monitoring solution that alerted them to the issue. Without such a software application or not taking the time to configure it correctly, it takes much longer to […]
-

Tracking Remote Employees’ Work Hours with Virtual Server Monitoring
With more people working from home due to the COVID-19 crisis, businesses of all sizes need to know when their employees are working. You need an effective way to track working hours and know what your employees are doing while they are working. One effective way to do this without having to invest in […]
-

Top 12 Advantages of Effective IT Monitoring Software
As a company’s IT systems develop and overlap in function, it becomes increasingly important that they be carefully monitored at all times. Active network monitoring helps to ensure central servers and systems are functioning as intended, while also allowing business management staff to keep an eye on employee activity in the process. Although […]
-

5 Things Only Experts Know About Server Monitoring
Server monitoring is a valuable tool when it is set up and configured correctly. With a server monitoring service, there are several things you can do if you have the right knowledge. Obtaining that knowledge is easy when you have experts in your employee or on contract. For others, access to experts is not […]
-

Use Active Directory Monitoring to Protect Remote Active Directory Logins
Active Directory (AD) is a process service that is used in Microsoft® Windows-based environments. It is responsible for authenticating users when they connect to servers and for authorizing access to different directories, files, and data. AD is also responsible for carrying out security protocols on all connected devices and computers. For example, there is […]