Category: How To
-
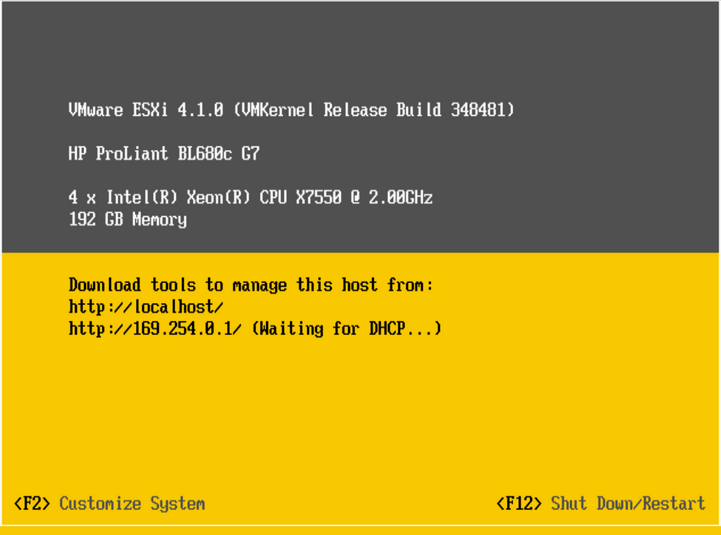
VMWare Virtualization – Deploying ESXi
ESXi is a powerful and popular virtualization tool made by VMWare that is used for the deployment and serving of numerous virtual computers. It is used as a standalone operating system and as such uses such components as a kernel. This operating system is the primary component that makes up VMware’s virtualization infrastructure suite. Pre-Installation […]
-
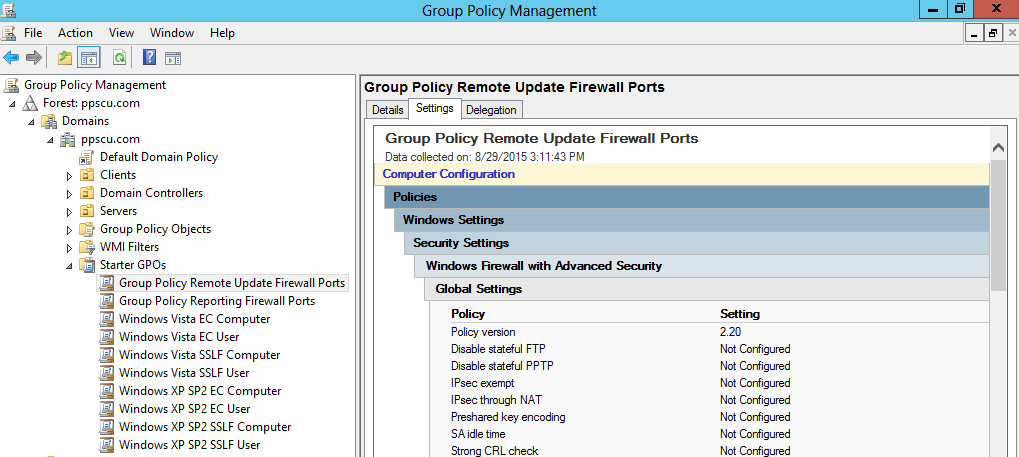
Remote Group Policy Update
With the release of Windows Server 2012 Microsoft added several new features to the server Edition. We’ve already discussed about some of these enhancements and today we’ll continue discovering another one, the remote group policy update feature. If you’ve worked on previous Windows Server Editions you know that the only way in which you could […]
-
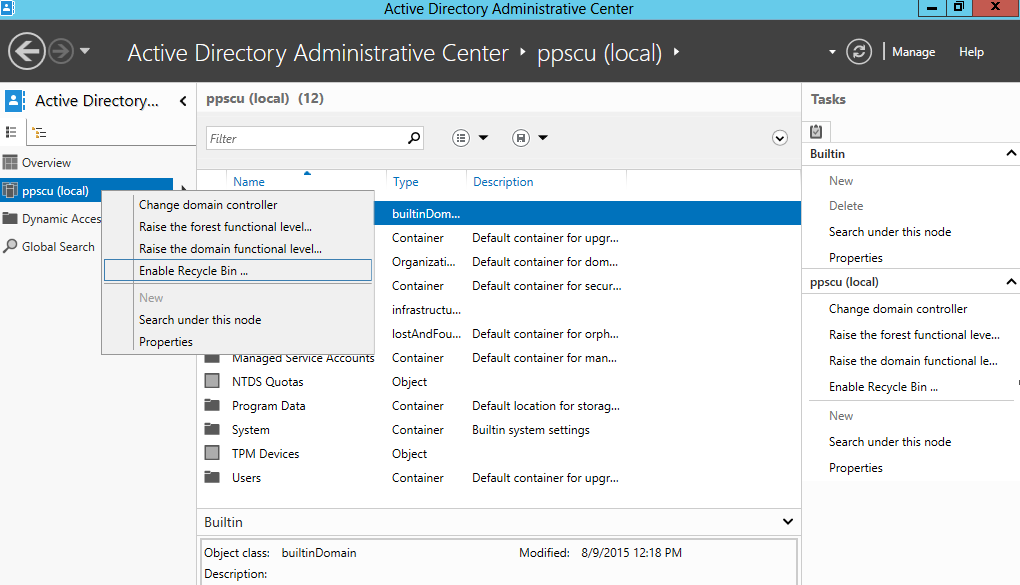
Restoring deleted objects from Active Directory using AD Recycle Bin
Windows Server 2008 R2 introduced a new way in which deleted objects can be recovered within an Active Directory infrastructure. This new feature added the so called AD Recycle Bin which enables Administrators to easily recover deleted objects. Before the Active Directory Recycle Bin was introduced, the restoration process of deleted objects was a painful […]
-

Installing and configuring DirectAccess in Windows Server 2012 – Part 2
By now we’ve learned about the main principles behind DirectAccess, its features, how to install it and we’ve started configuring it on a Windows Server 2012 box. I’ve previously pointed out that there are four main steps that needs consideration in order to successfully deploy DirectAccess, we’ve completed the first one in the last […]
-

Installing & Configuring DirectAccess in Windows Server 2012 – Pt.1
In the last article we’ve scratched the surface of the remote access technology available with Windows Server 2012, named DirectAccess. I’ve tried to cover the most important aspects of DirectAccess so we can go further and discover the practical usage of this feature. The method of installing and configuring DirectAccess has been simplified with the […]
-
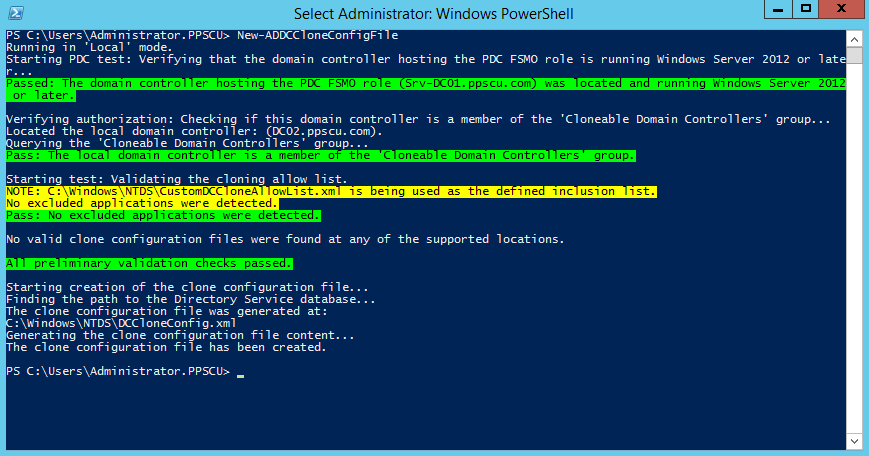
Cloning a Windows Server 2012 DC
With the release of Windows Server 2012 Edition, Microsoft featured a new way in which Domain Controllers can be deployed in an Active Directory infrastructure. This new method offers the possibility of cloning an active DC from your environment, but several requirements must be fulfilled before you can successfully clone a DC: A server that’s […]
-

DirectAccess in Windows Server 2012
I’ve been working previously with DirectAccess when it first appeared in Windows Server 2008 and although it was a bit difficult to install and configure, I managed to get the grasps of this technology. I haven’t been able to work on a real production environment and I still haven’t seen large DirectAccess implementations. One reason […]
-

WiFi Security: What You Should Know
Okay. So, you’re on the road. And you suddenly remember that vital email you neglected to send, before leaving the office. Or you get an urge to post that selfie you just took to your Instagram account. Laptop or mobile device at the ready, you connect to the Web using the free service at the […]
-

SSL And Beyond, Part 2: Compatibility & Deployment Across the Board
In our first installment we discussed the origins and development of the Secure Sockets Layer (SSL) protocol and considered its role in providing secure internet connections through encryption and the use of digital certificates. In this article, we’ll go further into the use case to discuss how applications are deemed compatible with SSL, and how […]
-

Hyper-V features Introduced in Windows Server 2012
As most of you already know, Hyper-V is the virtualization product that is shipped with Windows Server Editions. Microsoft has continuously added new features it and has really enhanced its capabilities. With Windows Server 2012 Edition, Microsoft introduced multiple features that allows further configuration to your virtualization environment. In this article we will discuss about […]