Category: General IT
-
Preparing a Disaster Recovery Plan for your Business – Cont’d
…cont’d from “How to Prepare a Disaster Recovery Plan (DRP) for your Business” Gaining Board Approval If the person compiling the DRP is not the owner of the business, then the owner’s approval and consent must be sought and gained. Whilst the IT professional will take into account all of the operational issues, things like […]
-

How to Prepare a Disaster Recovery Plan (DRP) for your Business
In the same way that formulating a business plan is essential when thinking of starting up a new business, formulating a disaster recovery plan (DRP) is essential once your IT infrastructure is in place, especially if you deal with data that requires auditing (such as customer credit card details, for example). The Basic Steps in […]
-

How to Choose the Best Antivirus Software for Your Situation
The Internet is littered with malware, viruses, trojans and other malicious pieces of software that could really ruin your day. That means it doesn’t matter if you’re a gamer or someone who uses an old family PC for browsing the web and checking email, you still need some sort of antivirus to keep yourself safe. […]
-
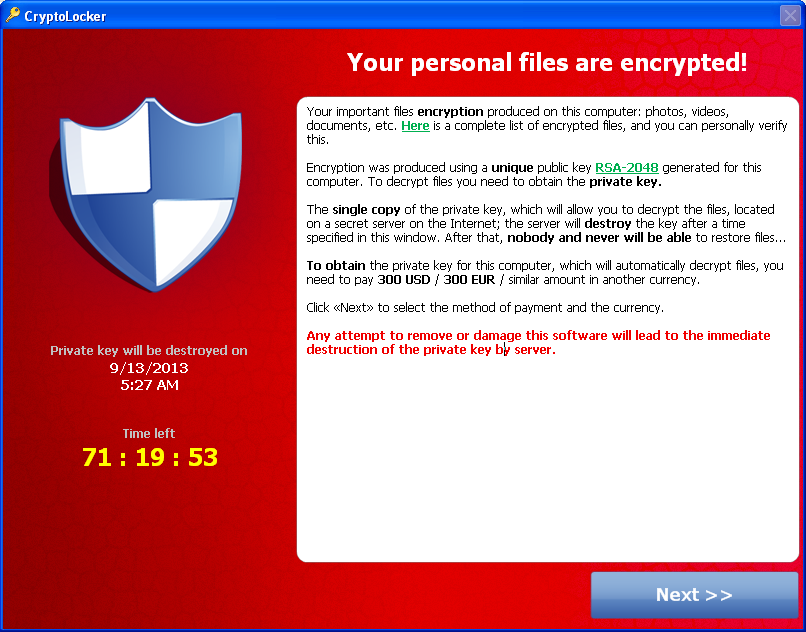
How Monitoring Software can Help to Protect Against CryptoLocker
If you spend a lot of time online, are pretty tech savvy or are in the technology sector, then there’s little doubt that you’ve come across the term ransomware here and there. In a nutshell, ransomware is a type of malware that infects a computer and effectively puts up a lock screen that holds the […]
-

3 Signs Your Web Server’s Security has been Compromised
More than ever, businesses have to be careful of attacks on servers and business networks to ensure that their data, and that of their customers’, are fully protected. This is especially true of sensitive data such as credit card and personal details, especially as a failure to protect this could incur a hefty fine when […]
-

Fixing a Buffalo LS-QV4.0TL/R5 NAS
We got a little NAS device to play around with, do some back ups to, etc. The Buffalo LS-QV4.0TL/R5 comes with 4 x 1TB drives, but we wanted some more space, so we replaced the 1TB drives with 2TB drives. Mistake 🙁 It turns out the OS is on those drives (duh!). What you’ll see […]
-

An Overview of the New Windows 8 Enterprise Edition
Not since the launch of the Windows Vista operating system has there been so much negativity about the latest upgrade of Windows for consumers. But is it really justified, or is it simply misinformation and/or the lack of information that has driven large swathes of the business community to avoid it thus far? Setting […]
-
Encrypt Hard Drives Using BitLocker Drive Encryption-Cont’d
Part 2… From previous experience I can tell you that this operation can take several hours if your hard drive contains a lot of data, so make sure that the laptop stays on until the encryption is complete. Upon finishing the operation, you will receive the following message: If you are encrypting a system […]
-

Encrypting Your Hard Drive Using BitLocker Drive Encryption
In this article, we will talk about one of the most effective and powerful encryption mechanisms available with Windows Systems. BitLocker is a feature that enables you to encrypt your hard drive data so that it becomes practically impenetrable by hackers. This means that even if your portable device gets in the wrong hands, without […]
-
Install & configure Windows Server Update Service (WSUS) – Pt 2
Cont’d from… “How to install & configure Windows Server Update Service (WSUS)” Choose the upstream server that you are going to use for receiving the updates. In this demonstration we are going to receive updates directly from Microsoft servers. On the Proxy Server page, you can enter the proxy server address and credentials if […]