Category: General IT
-

Ransomware: 11 Steps You Should Take to Protect Against Disaster
The frequency and volume of ransomware attacks have increased dramatically in the past few years. Few people in the tech industry will forget the 2017 WannaCry attack, which infected over 200,000 computers in 150 countries worldwide and brought down part of the U.K.’s National Health Service, or the 2019 RobbinHood attack, which brought the Baltimore […]
-

7 Tips to Prevent Ransomware
Ransomware is a malicious type of software that’s used to extort money from victims. It almost always promises to restore the data it encrypts or the operating system it locks, in exchange for a large sum of money. Networks seem to face threats from all directions, but there are ways to prevent malware attacks. Specialized […]
-

Data Loss Prevention and Security Basics You Need to Know
Cyberattacks are the “buzz word” that you hear when a company’s data has been breached. Sometimes the breach results in data being released on the internet. Other times, the hacker holds the data ransom in exchange for a large monetary payout. Data loss prevention and protection should be at the top of your list. […]
-

Server Monitoring and Alerts – Getting Past Common Obstacles
Keeping a server running optimally on a consistent basis involves managing multiple system elements simultaneously. Automated scripts and specialized software can handle the tasks your server needs to complete on a daily basis—but when one of these experiences an error, it can throw the entire system off. Monitoring makes up for other programs’ error-handling […]
-

VPN vs. Remote Desktop – Gateway Security Concerns
VPNs and Remote Desktop Gateways are two different tools used to achieve similar goals. That is: access content or software remotely and securely, and improve the overall freedom of the user – whether that’s from prying eyes or the need to have physical access to their business network. But while each option can be […]
-

How To Keep Track Of Your Android Applications
Keeping track of application usage and the installation of software on your Android phone or tablet is an essential activity, both for device management and your overall security. In this regard, it’s also advisable to monitor how your Android applications are tracking you, in terms of your physical location, activities on the local device, and […]
-

Blocking USB Drives For Work From Home Employees
With so many people working from home, the perimeter of corporate data safety has suddenly grown very large, in many cases encompassing employee home computers. Data loss prevention (DLP) was challenging enough already, but now it takes on even more importance. One way that data can escape the corporate network is by […]
-

COVID-19 Statement
Dear Customers, We here at Power Admin want to assure you that we take the health and well-being of our community, customers, and associates very seriously. Like you, we’re closely monitoring the quickly developing effects of the Coronavirus (COVID-19) pandemic. Our employees are practicing their social distancing skills by remotely working from the […]
-

How To Secure Home Computers That Are Connected To Corporate Networks
Coronavirus is changing everything. But amid all the talk of shut-downs, quarantine, and stock market crashes, another huge impact of the current crisis has been a little overlooked: it’s consequences for cybersecurity. With hundreds of thousands of employees now working from home – in the US, Europe, and all over the world – many […]
-
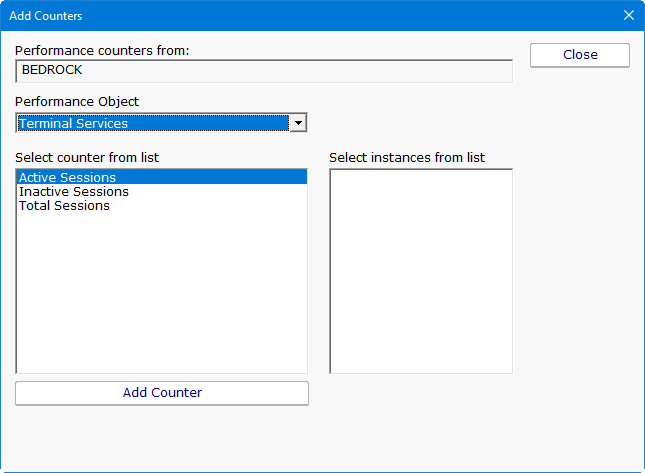
Monitoring Remote Desktop (RDP) Performance
With so many people working from home now, Terminal Servers and Remote Desktop Gateways are surely getting exercised like never before. Perhaps you want to monitor them to see how busy they are, and alert if there are problems. Below are a few ideas. CPU of Course Naturally you need to monitor the server’s CPU […]