Category: General IT
-

Reducing the Risks of File Sharing
Exchanging ideas and sharing information are integral parts of working life. Ever since computers and digital technology became central to the way we work, people have exploited various means of passing documents and files containing text, images, and audio-visual data on to colleagues, suppliers and partners. As technologies have evolved, the methods have improved.…
-

Another email Hack: Should We Worry?
Each time a major email service or social media platform gets hacked, the incident generates exciting headlines in the media. But behind the hype there’s a very real tale of anxiety for all the users concerned. Has vital information been stolen or compromised? Are funds being siphoned off, into the hands of criminals –…
-

Best Practices for Software-Defined Storage
Currently being celebrated as the revolutionary new face of IT infrastructure, software-defined networks or SDNs have gained a lot of hype, but not too much practical guidance in the industry press. In this article, we’ll suggest some best practices to enable you to make the most of the data storage capabilities of this evolving technology.…
-
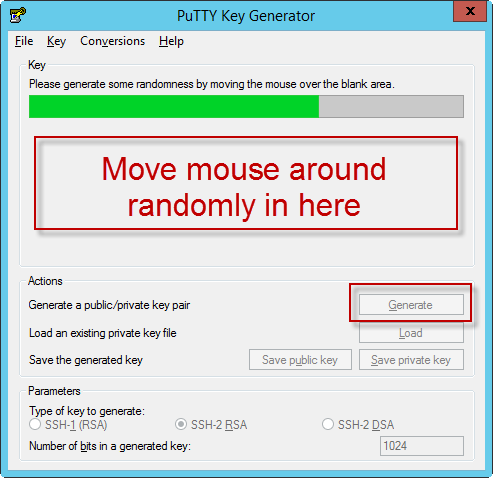
Enabling Public/Private Key SSH Authentication on VMWare ESXi from Windows
Having just struggled with this for a while, I thought I’d record the steps I took. They’re pretty easy once you figure them out (isn’t it always that way!). First, we need to enable SSH connections to our ESXi server. In the vSphere client, go to Security Profile. If you don’t see SSH, you can…
-

Bring Your Own Everything Revisited
As advances in technology bring about a convergence of portable hardware, virtualized resources, and remotely hosted tools and platforms, there’s been a corresponding increase in the use of personal devices and related matters in the workplace and in public institutions. This trend has implications for the management, deployment, and security of IT resources – some…
-

Unmasking the Imposters, Part 2: Detection and Damage Control
In the first of this two-part security report, we discussed the threat presented to individuals and enterprises by malicious outsiders posing as members of an organisation itself, or representatives of a trusted external institution like a bank or popular online resource. We looked at how these imposters are refining their methods of extracting funds or…
-

Unmasking the Imposters, Part 1: An Evolving Threat
We’ve come a long way, since the first large-scale outbreaks of advanced fee fraud and email account hacking, back in 1986. In the years to date, cyber-criminals and fraudsters have stepped up their game, considerably – to the point where (in some unfortunate organisations) it’s nearly impossible to distinguish between genuine staff and authorised…
-
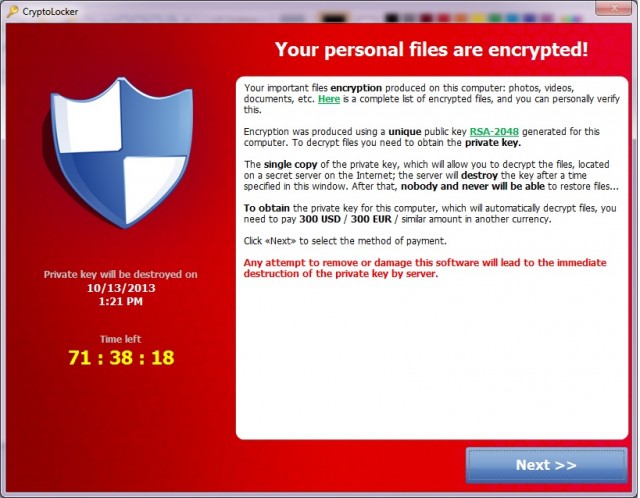
Early Detection and Prevention of CryptoLocker
In case you haven’t heard, CryptoLocker is a popular form of the ransomware malware that encrypts your files and then holds them hostage. Generally you have to pay to get them decrypted. If you have a backup of all of your data, you might be able to avoid the payment. If you have a backup……
-

Maintaining a Secure SDN
As technologies continue to evolve, the nature of IT infrastructure is changing. Virtualisation, hyper-convergence and increased connectivity are presenting fresh opportunities for malicious intruders to gain access to networks. One of the platforms presenting new possibilities to both network administrators and hackers is SDN. What is SDN? A software-defined network or SDN is an…
-

Enterprise Applications of Artificial Intelligence
Much of our conception of Artificial Intelligence or AI has been shaped by popular movies: from the homicidal Red Queen of “Resident Evil”, to the J.A.R.V.I.S. operating system / virtual butler that provides logistical support to “Iron Man”. Extremely advanced intelligence and – in some cases – living machine consciousness. We’re not quite…