Category: General IT
-

How Cyber Attacks Affect Us
Another nice infographic from Utica College. . Source: Utica College Cyber Security
-

Micro-Segmentation Best Practices
With the growth of software-defined networking (SDN) and the evolution of software-defined data center (SDDC) technologies, network administrators, data center operators and security officers are increasingly looking to micro-segmentation, for enhanced and more flexible network security. In this article, we’ll be considering the nature and characteristics of the process, and looking at ways to…
-

Cyber Security Career Options
The folks over at Utica College have put together a great infographic that we wanted to share. Source: Utica College Cyber Security
-

Strategies For Managing Co-Location
Outfitting, maintaining and managing a data center can be an expensive, time-consuming and labor-intensive process – one which may be beyond the budgetary or human resources of smaller-scale enterprises. In other instances, an organization’s data management and processing needs may not warrant the investment in a full-blown data center of their own. For circumstances…
-

Reducing The Stress Of Data Migration
Life is never static, and for businesses the occasional relocation of data archives, mission-critical applications, infrastructure and services may prove necessary. It can be a complex and at times risky endeavor. There are ways to make the process less stressful, and to reduce the potential for such migrations to be costly, disruptive, or in some…
-
Data Migration Infographic
-

Enterprise Encryption Best Practices
Whether it’s to safeguard internal protocols and hierarchies, or to guard against attacks and data breaches in the escalating scale of current cyber-threats, implementing controls on the way information is transmitted and shared is more crucial to the enterprise than ever. Encryption has been and remains an essential aspect of this process. But how best…
-
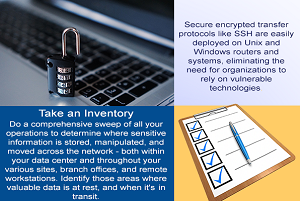
Enterprise Encryption Best Practices – Info Graphic
We hope you like this infographic. We’ll have a follow up article posted on October 18th with more information 🙂
-

Reducing Downtime While Backing Up AWS EC2 Instances
We’re big fans of AWS and use several of its services. One service we use is EC2 – it costs much less than having a dedicated server and still gives you full control of the server. One issue is being sure we can bring the server back up in case it crashes, or the…
-

15 Ways to Protect Your Business from Hackers
Today we have a guest post from Sachin over at FromDev.com. And without any further ado, we’ll turn it over to Sachin. There is no business in this internet age that cannot be hacked. Most skilled hackers can hack into any system. It has happened to most of the top tech businesses in the past,…