Author: William Thompson
-
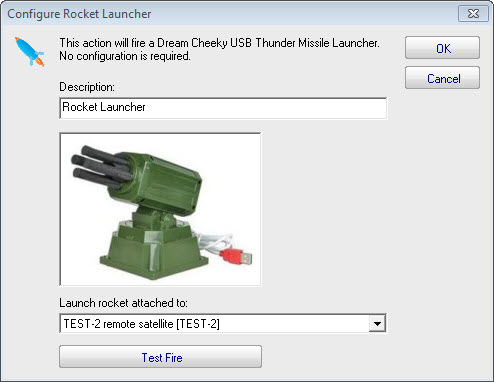
USB Rocket Launcher as an Alert
Think server monitoring can’t be fun? Think again! Try out our USB Rocket Launcher alert. PA Server Monitor can launch small USB rockets as an alert type. 🙂 The Dream Cheeky Thunder USB Missile Launcher (purchased separately) can be attached to the server where the PA Server Monitor is installed via the USB cable. The…
-
Are Windows 9 Rumors True?
Microsoft is set to announce Windows 9 at the Build 2014 Conference Windows 8 wasn’t exactly a resounding success. Much of what was updated in the OS was necessary, but the application of the new features was in many instances poor. Windows 8 attempted to stitch together the desktop and mobile experiences and this was…
-

How Can Server Monitoring Improve Performance?
It’s important to maintain a careful watch over a company server as misuse of this technology can lead to data loss and it can incur financial costs. Server monitoring tools provide administrators with an easy way to maintain a vigilant approach as they provide alerts and function to keep the administrator up to date and…
-

Server Monitoring Best Practices
As a business, you may be running many on-site or Web-based applications and services. Security, data handling, transaction support, load balancing, or the management of large distributed systems. The deployment of these will depend on the condition of your servers. So it’s vital for you to continuously monitor their health and performance. Here are some…
-

Ensuring HIPAA Compliance
HIPAA sets the standards for the protection of PHI (Private Health Information) and ePHI belonging to those people who receive medical care from your business. So, if you are: A covered healthcare provider like a hospital or individual medial practitioner A business associate of these providers (including the private sector or 3rd party administrator) A…
-

9 Common Problems in Windows 8.1
Windows 8.1, Microsoft’s new operating system, is not without flaws. Many of the issues relate to the confusing interface but some are indicative of deeper problems. Windows 8 has bugs. Which, to many users, is probably not a surprise. Fortunately however, like Microsoft’s preceding OS, there are solutions. Microsoft is a company moving forwards and…
-

Measuring Disk Latency-Windows Performance Monitor
Physical Disk Latency is, in a nutshell, a measure of the delay from when a disk Input/output (I/O) request is created until it’s completed. It determines how fast a computer responds to various tasks and increased latency can be a sign of a problem with the system, or simply that it’s overworked. In the old…
-

Recovering from a Windows Server Crash
There’s nothing worse than the plummet your gut experiences when you’ve just been told your servers have crashed. Thankfully all isn’t lost. Essential data can be restored through a number of means. Make use of a bootable USB flash drive, install from the Windows Installation media or restore from a previous back up. If all…
-

Auditing Windows Server 2012
Current business modeling relies heavily on the virtualization of its network. Many transactions and interactions are now carried out by employees and contractors using mobile devices. Doctors and nurses are no longer relying solely on paper-based note recording and filing, making full use of tablets and laptops to handle patient information. Trade, salespeople and contractors…
-

Is Your Wireless Network Vulnerable to Packet Sniffers?
Almost every company has a wireless network in effect to some extent. It´s a part of the modern workplace and keeps computers, printers and other devices talking to each other and working smoothly. Every wireless network is a potential entry point for determined hackers, though, who can hack your system from a nearby coffee shop,…