Author: Doug N
-

How Cyber Attacks Affect Us
Another nice infographic from Utica College. . Source: Utica College Cyber Security
-

Have you tried Dynamic Server Lists?
Have you tried the Dynamic Server List monitor? If not, you’re missing out on a powerful feature! The Dynamic Server List monitor can be run as a Global Monitor, from Advanced Services > Global Monitors. It lets you create a list based on a large number of possible criteria, such as: • Does the server […]
-

Cyber Security Career Options
The folks over at Utica College have put together a great infographic that we wanted to share. Source: Utica College Cyber Security
-
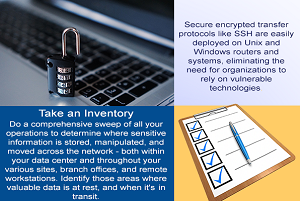
Enterprise Encryption Best Practices – Info Graphic
We hope you like this infographic. We’ll have a follow up article posted on October 18th with more information 🙂
-

Reducing Downtime While Backing Up AWS EC2 Instances
We’re big fans of AWS and use several of its services. One service we use is EC2 – it costs much less than having a dedicated server and still gives you full control of the server. One issue is being sure we can bring the server back up in case it crashes, or the […]
-

15 Ways to Protect Your Business from Hackers
Today we have a guest post from Sachin over at FromDev.com. And without any further ado, we’ll turn it over to Sachin. There is no business in this internet age that cannot be hacked. Most skilled hackers can hack into any system. It has happened to most of the top tech businesses in the past, […]
-

Why Network Monitoring is Important for Your Business …
Check out our post over at SiteProNews
-

The Costs of Not Monitoring
Why monitor your servers? As with all resources, computer resources are limited. That means limited work can done by the CPU, limited information can be held in system memory for use, and limited data can be stored on disk. When a system has all of the resources it needs, it generally runs fine. But […]
-
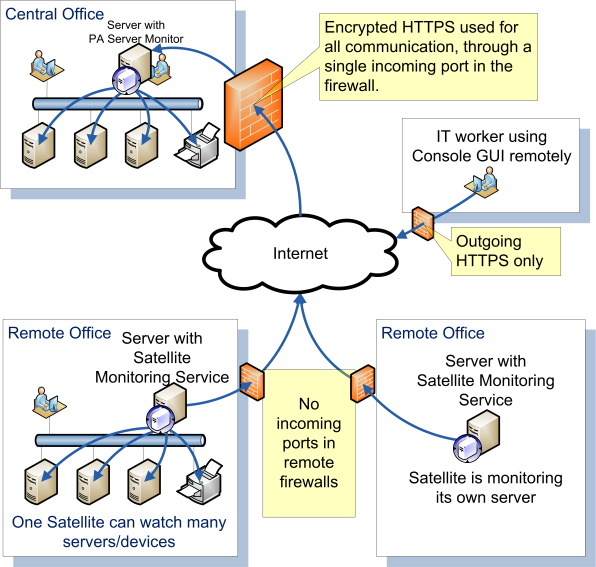
Free and Secure Remote Access? Sort of …
Recently, GoToMyPC forced all customers to reset their passwords. They were not hacked, but rather saw that hackers were attempting to access their customers’ computers using credentials that had been hacked from other places. This seems like a good opportunity to show off how PA Server Monitor can allow remote access in a completely […]
-

What is Cryptolocker Ransomware?
Cryptolocker is a well known malware (software that does harm) of a particular variety: ransomware. Some malware (like computer viruses) delete and destroy. The hackers that create ransomware have other motivations: money. Ransomware Ransomware does something to your computer, and then demands a ransom payment to get your computer back to the way it used […]