Author: Doug N
-

Windows 2003 – Time’s Up!
As we speak with customers we hear about what they are using in their IT infrastructure. And we know there are still a fair number of organizations that are using Windows 2003. To be honest, it was a great workhorse — it did it’s job well and was pretty solid. However, support has ended and […]
-

Dilbert’s take on Network Monitoring Software
DILBERT © 2012 Scott Adams. Used By permission of UNIVERSAL UCLICK. All rights reserved. Given that Dilbert said this in 2012, his stance is that good network monitoring software takes a solid 28 man-years to create. Joel Spolsky famously said “good software takes ten years”. We tend to agree. PA Server Monitor is now more than 11 years old, […]
-

LinkedIn Feature: The Cost Of Downtime
Hello All! Now, because we know that you simply cannot get enough of the superlative content that we regularly produce for you here on our blog at PowerAdmin, we thought that we’d create some more for you lucky people. And so, starting today (February 11th 2015), we are posting up a very special extended 3-part […]
-

Shellshock vulnerability – worse than HeartBleed 🙁
Do you remember HeartBleed from a few months back? There’s another huge vulnerability that just came to light: Shellshock. And this one is much worse than HeartBleed 🙁 Shellshock is based on a vulnerability in the Unix/Linux bash command processor. Bash can be forced to execute commands stored as ‘environment variables’ and unfortunately, many programs […]
-

Server Monitoring Best Practices
We often get asked about suggested practices for monitoring servers and it’s a legitimate request – there are so many moving parts it’s hard to know where to start. There are two things you want your monitoring to do for you: Watch systems 24×7 and alert you if there is a problem Show you current […]
-
The Heartbleed Bug – PA Product Upgrades
On Monday, April 7th, the OpenSSL Project released an update to address a serious security issue – CVE-2014-0160 – nicknamed “Heartbleed”. PA Server Monitor, PA Storage Monitor and PA File Sight all use OpenSSL as part of the internal HTTPS server. On April 10th, we released version 5.4 of each of the above applications, which […]
-

Fixing a Buffalo LS-QV4.0TL/R5 NAS
We got a little NAS device to play around with, do some back ups to, etc. The Buffalo LS-QV4.0TL/R5 comes with 4 x 1TB drives, but we wanted some more space, so we replaced the 1TB drives with 2TB drives. Mistake 🙁 It turns out the OS is on those drives (duh!). What you’ll see […]
-
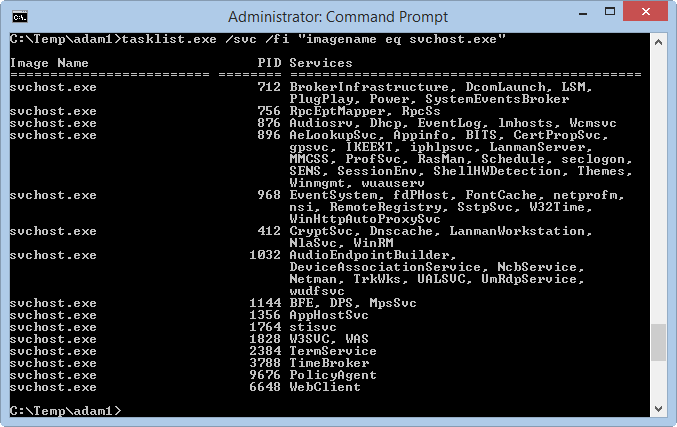
Windows 2003 and High CPU Usage in Svchost
Windows 2003 is getting a bit long in the tooth, but we’ve got a number of customers that are still happily using it, and for good reason — it’s a solid work horse of an OS. We’ve recently come upon an issue where some of our 2003 servers in the lab were pegging the CPU […]
-

Building OpenSSL with Visual Studio 2012 for 32- or 64-bit
For our programmer (dev/ops) friends, we thought we’d share a little about building OpenSSL. There are a lot of examples online, but we kept finding they had little glitches, not quite complete, etc. So here is how we built it: You need Perl installed. ActiveState’s free community Perl install is just fine. First, you need to […]
-

SHA-1 Hashing Algorithm & Windows 2003
In 2012, the U.S. National Institute of Standards and Technology (NIST) indicated that the SHA-1 hashing algorithm should no longer be used by federal agencies. Our products use self-signed SSL certificates by default (you can replace that with your own certificate), and SHA-1 is used as the signature algorithm. We started researching moving to SHA-2 […]