Author: Doug N
-
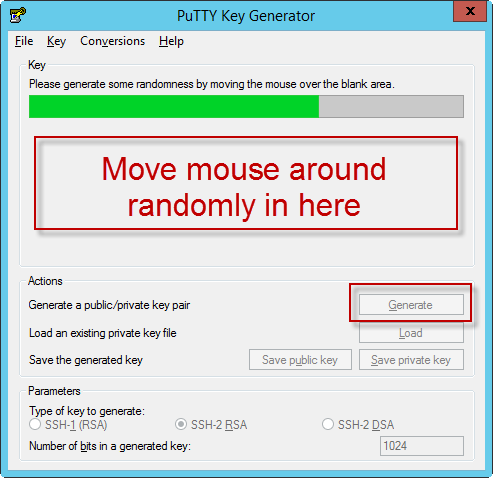
Enabling Public/Private Key SSH Authentication on VMWare ESXi from Windows
Having just struggled with this for a while, I thought I’d record the steps I took. They’re pretty easy once you figure them out (isn’t it always that way!). First, we need to enable SSH connections to our ESXi server. In the vSphere client, go to Security Profile. If you don’t see SSH, you can […]
-

Power Admin Network Technology Scholarship
Power Admin is delighted to announce the Power Admin Network Technology Scholarship. The program will award $2000 to a diligent student each year. The scholarship is intended to help young students afford the increasing cost of tuition and help them along the road to a future career in the networking technology/IT field. Before you […]
-
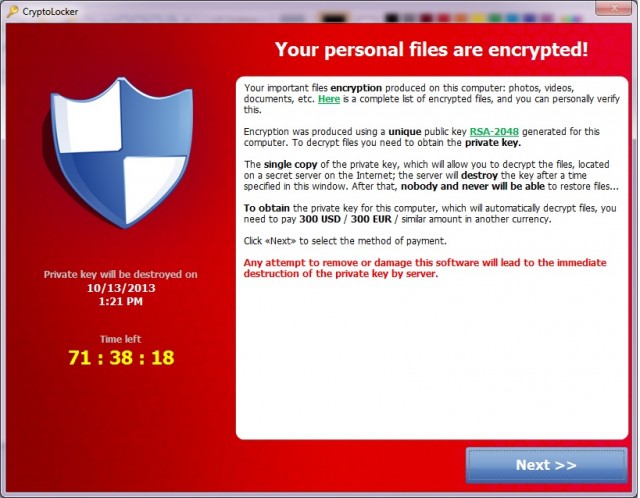
Early Detection and Prevention of CryptoLocker
In case you haven’t heard, CryptoLocker is a popular form of the ransomware malware that encrypts your files and then holds them hostage. Generally you have to pay to get them decrypted. If you have a backup of all of your data, you might be able to avoid the payment. If you have a backup… […]
-
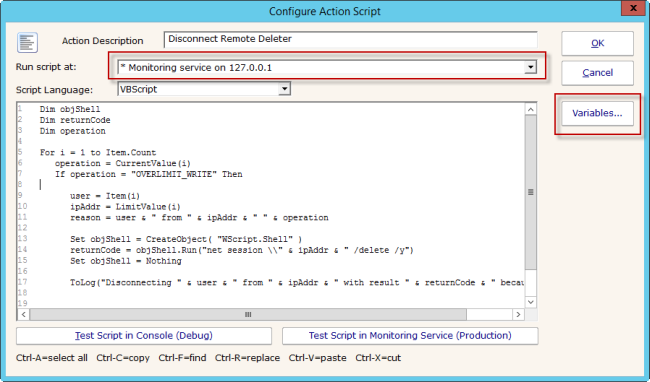
Early Detection and Prevention of CryptoLocker – The Response Scripts
In the previous post, I mentioned a couple of ways customers are working on detecting CryptoLocker attacks. In this post, I’ll share a few scripts they use in response. Ideally, you could quarantine the user’s computer from where the attack is coming from. In practice, that can be tricky. Note that these responses could be […]
-
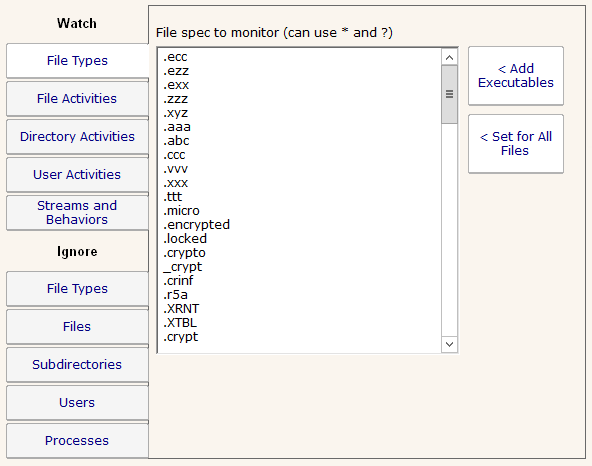
Cryptolocker File Extension List
There is a thread on Reddit that lists many known Cryptolocker file extensions (both the extension that the newly-encrypted file gets, and the ransom note file). A number of customers have asked to be able to more easily paste this list of file names into the list of file types to watch, which is […]
-

51 DevOps Influencers to Start Following Today
While the objectives of DevOps are to stop wasting time and money on IT projects that become slow, unwieldy and incredibly bureaucratic, the whole concept is really about people- perhaps more so than technology. It’s probably for this very reason that a community of evangelists and advocates has grown and become instrumental in sharing […]
-

Legacy Windows Survey
Have you wondered how many companies are still relying on old versions of Windows that are no longer supported? Windows 2000, XP and 2003 for example? Would you like some help convincing your boss that it’s time to upgrade? Take this quick 3 question survey and together we’ll all find out what that landscape […]
-
PA Storage Monitor version 6 Beta!
PA Storage Monitor version 6 has entered Beta! Exciting new features in version 6 include: Monitor template support PagerDuty alert action Desktop notification widget Configurable charts with configurable scaling Icons for servers and groups Dynamic server lists and groups based on server properties and more… You can find more information here. The PA […]
-
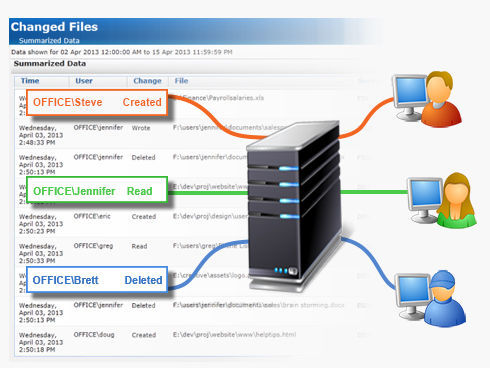
PA File Sight version 6 Beta!
PA File Sight version 6 is now in Beta! For those not yet in the know, PA File Sight tracks who is accessing files on a Windows server. Lots of software can tell you who created or saved a file. Almost no products can tell you who is reading from a while, or who deleted […]
-
Simulating a Large Network
We live, eat, breathe and love monitoring here at Power Admin. So we’re always looking for ways to improve. One way is to scale our software to handle ever increasing loads. Some of our larger customers (the largest anti-virus and computer security software company in America which starts with ‘Sym’ and ends with […]