Author: Doug N
-

OpenSSL v3.0.0 – v3.0.6 critical vulnerability
OpenSSL is the backbone of secure Internet communication. It has two currently active and supported development branches: version 1.1.1 and version 3.0. It has recently been discovered that all current versions of OpenSSL 3 (3.0.0 through the current 3.0.6) have a critical security vulnerability, and must be upgraded to a new version immediately. …
-
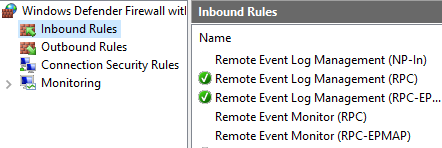
Event Log Monitors Failing? Check Windows Firewall
In the past week or two we have been receiving a lot of email from customers reporting that their Event Log Monitor has suddenly started failing on a number of servers. We don’t have proof, but we’re guessing a recent Windows Update must have disabled the Remote Event Log Management rules. (Edit): Confirmed! Thanks…
-

What Should You Do When You Receive Event Log Monitor Alerts?
When you are installing PA Server Monitor, you will need to configure what occurs when there are event log monitor alerts. You typically set this up during the initial install. However, it is not uncommon to want to make changes and updates or even add new events to your server monitoring software as you become…
-
Which Event Log Events Should You Worry About?
When you are configuring your event log monitor settings, you need to decide which event log events you need to worry about. Event logs are generated for a wide array of processes, applications, and events. Logs will record both successes and failures. As such, you need to decide what data is most vital and needs…
-

How to Configure PA Server Monitor to Monitor Your Event Logs
Did you know that you could configure PA Server Monitor’s Event Log Monitor feature to monitor one or more of your event logs? The event logs can include standard application, security, and system logs, as well as any custom event logs you want to monitor. With our server monitoring software, you have complete control and…
-

What You Need to Know About Server Security in 2021
How often do you check your event log monitor for potential security breaches? Did you know that many potential security breaches, events, and other problems are logged to event logs? Unfortunately, even the most skilled IT professionals have a hard time making sense of what to watch for that could indicate security issues or even…
-

10 Server Maintenance Tips for Efficient Server Maintenance
Just like your commercial vehicles or HVAC systems, servers require regular maintenance to ensure they are operating effectively and optimally. So, we decided to compile a list of server maintenance tips you should be doing. Keep in mind, these server maintenance tips are meant to be used as a guide to help you develop…
-

The Top 5 Benefits of Temperature Server Monitoring Solutions
Your servers generate heat—this is a fact common with any type of electronic device. The amount of heat they generate will vary, depending on where they are located and the number of servers in use. For example, a small business may have only one or two servers that are stored in a small server…
-

Recommended Hard Drives Operating Temperature Range
Did you know that hard drives have a recommended operating temperature range? Most people do not think about what happens when they turn on their computer or server and the hard drives begin to whirl around inside. Even if you have the newer solid-state drives (SDDs), you still need to know the recommended hard drives…
-

Recommended Server Room Temperature and Humidity
What are the ideal server room temperature and humidity levels where you store your servers? This is an important question you should know the answer to whether you are responsible for managing racks of servers or a small business owner with a single server. Servers house your data, files, and other information to make…